
by Chad Ostreicher | | Best Practices, IT infrastructure, IT Services, Security, Software, Tips
With 2022 being just days away, it is time for you to start planning, strategizing, and enacting reasonable security measures to protect your business from cyberattacks and IT issues. We’re sharing our security checklist that will include the top IT-related New...

by Chad Ostreicher | | IT Services, Ransomware, Remote work, Security, Tips
The Holiday Season is upon us, and unfortunately, the opportunities for scammers are through the roof. It’s important to know what fraudulent schemes to watch out for to avoid falling victim to a scammer. Let’s look at some warnings before we dig deeper...
by Chad Ostreicher | | Hardware, IT Services, Remote work, Security, Tips
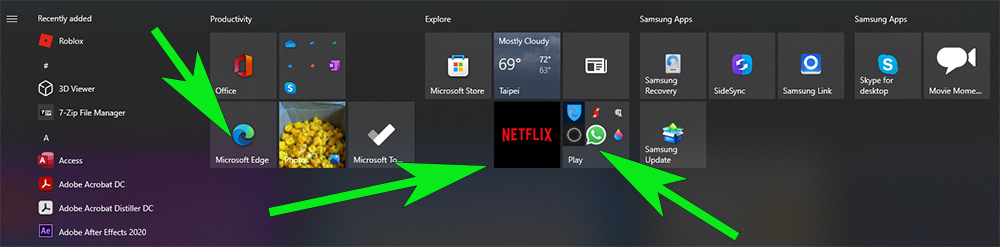
Bloatware is software that comes pre-installed on a computer, smartphone, or tablet but isn’t necessary for the device to operate. Some manufacturers include pre-installed bloatware as an incentive to get you to buy their devices, while others do it because they...

by Chad Ostreicher | | Best Practices, Ransomware, Security, Tips
Who doesn’t want to skip going through airport security during the holiday season? If you’re trying to skirt the airport screening process, you are the perfect target for the TSA PreCheck renewal scam that has been going on since March. Scammers are using...

by Chad Ostreicher | | Best Practices, Cloud Services, Hardware, IT infrastructure, IT Services, Security, Tips
When securing your printer or copier, these machines are often overlooked because most people think, “who is going to hack my printer?”. It also may be because it’s a device that doesn’t hold much personal information or data that hackers might...






