
by Chad Ostreicher | | IT infrastructure, IT Network, Security, Tips
As the race to keep up with the lightning speed of technology intensifies, Zero Trust is the savvy strategy that smart companies are embracing to stay ahead of the game. Gone are the days of blindly trusting traditional security models! We must evolve and adapt to the...

by Chad Ostreicher | | Best Practices, Security, Tips
Have you ever opened your email inbox to find dozens of spam messages? If so, you’re not alone. Distributed Spam Distraction is an attack that inundates an individual or company with a deluge of messages, making it almost impossible to identify authentic...
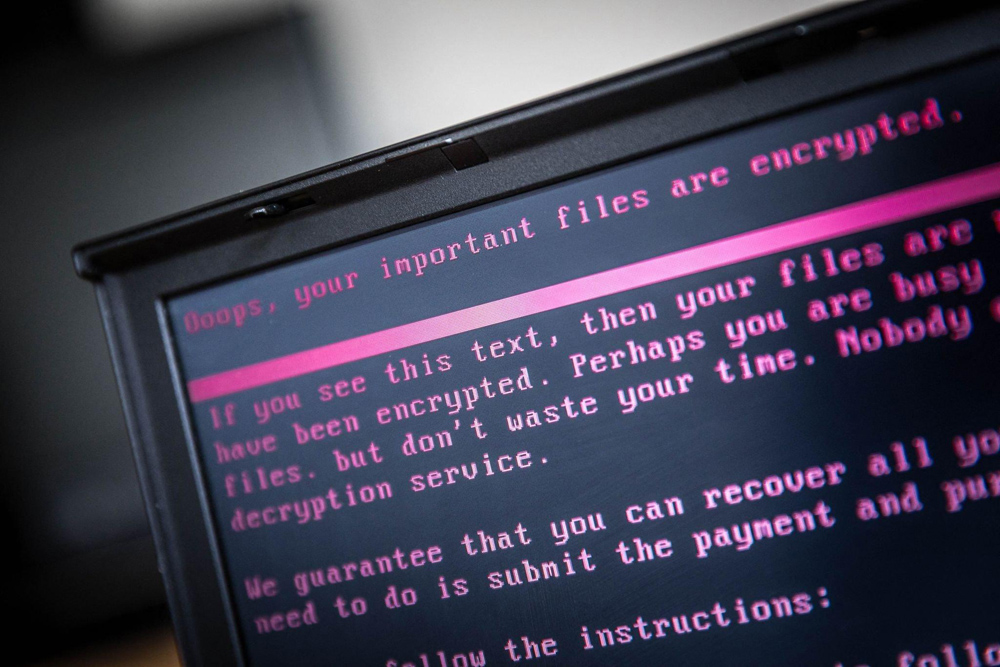
by Chad Ostreicher | | IT Network, IT Services, Ransomware, Security
Ransomware is a cyber threat everyone should worry about because it has affected millions of individuals and organizations across the globe over the last few years. It is a form of malware that encrypts a victim’s files and demands a ransom payment be made in...

by Chad Ostreicher | | Password Management, Security, Tips
With the ever-increasing number of online services and platforms, remembering many passwords for them has become almost impossible. We’ll explore the safety of password autofill, its benefits, and its potential risks. From man-in-the-middle attacks to...

by Chad Ostreicher | | Best Practices, Ransomware, Security
Ransomware is malicious software designed to encrypt data or block access to a device until a user pays the hacker for the decryption key. It can be delivered via email, malicious links, or unsecured networks. Once ransomware infiltrates a system, it usually displays...
by Chad Ostreicher | | Security
Robots have been a staple of science fiction for decades, but they are no longer just the stuff of dreams. We now have self-driving cars, military robot dogs, and even robots that can hack into computer systems. As human intelligence continues to evolve...







