Have you ever opened your email inbox to find dozens of spam messages? If so, you’re not alone. Distributed Spam Distraction is an attack that inundates an individual or company with a deluge of messages, making it almost impossible to identify authentic messages from spam.
There are various types of Distributed Spam Distraction attacks, and we will touch on the most commonly used methods you need to know about.
Table of Contents
Types of Distributed Spam Distractions
A common type of spam attack that has evolved over the years is Distributed Spam Distraction (DSD). This phenomenon has become more dangerous with the growth of sophisticated malware threats, covert approaches, and email bombs that can disrupt the day-to-day operations of financial institutions.
Traditional Spam
Traditional spam is a common attack that can leave your email inbox flooded with thousands of unsolicited messages. These messages can include fraudulent purchases, payment slips, and suspicious links to steal personal information or install malware on your device. The sheer volume of emails can make navigating through your inbox and finding important messages challenging.
To prevent traditional spam, robust spam filters must be used to detect and eliminate spam emails before they reach your inbox. This way, you can focus on the messages that matter and avoid the risk of opening unsolicited messages with harmful links or fraudulent information.
In addition to spam filters, you must be cautious whenever you receive an email with suspicious links or foreign transactions. Always hover over the hyperlink to check the URL and verify that the site is legitimate before clicking. If you receive an email with a notification of a purchase you do not recognize, do not click on links or provide personal information. Instead, contact your financial institution to verify the message’s authenticity and report any fraudulent activity.
Nonsensical Emails
Nonsensical emails use random excerpts of text that make no coherent message. This type of DSD makes it challenging for spam filters to pinpoint and block because unrelated words are tough to detect. They often contain meaningless and jumbled text with no clear message or purpose. They can be easily overlooked by email recipients and seen as benign. However, these messages can be part of an email bombing campaign that sends dozens of emails to distract users.
To identify nonsensical emails, look for messages that include random phrases or sentences that do not seem to make sense or are poorly written. These emails can be identified by their subject line, sender address, or preview text. They may also contain suspicious links or attachments that could infect your device with malware, a significant threat to your online safety.
Be cautious because opening spam emails can pose a malware threat and lead to identity theft, unauthorized purchases, and various illegal activities. Cybercriminals may also use these emails as a cover to carry out more dangerous attacks such as phishing, spear-phishing, and email spoofing.
Dangerous Links
Distributed Spam Distraction (DSD) attacks are not limited to inundating email inboxes with a deluge of spam messages. Still, they can also be the source of malware threats. Dangerous links are one-way malicious actors infect systems with malware.
Email users can accidentally click on dangerous links when they look like legitimate links to access useful content. However, instead of helpful information, the link directs the user to a webpage that installs malware on their system, leaving their device or system vulnerable to cyber-attacks.
The most common way malware threats are carried out is through phishing scams. Attackers send unsolicited emails claiming to be from a legitimate source like a bank or online shopping platform, luring users to click on the link in the email. These are often disguised as legitimate emails, such as payment confirmation messages or login requests.
Fraudulent payment slips and fake login pages for financial accounts are some examples of dangerous links that cybercriminals can use to gain unauthorized access to the victim’s device or sensitive data.
To recognize and avoid these links, users should authenticate the sender and refrain from clicking on links in unsolicited emails. Multifactor authentication can add an extra layer of security by requiring users to provide two or more authentication types, making it less likely for attackers to gain unauthorized access. In addition, email filters can automatically identify and block unsolicited messages containing dangerous links, making it easier for users to avoid them.

Unfamiliar Transactions and Payment Confirmation Messages
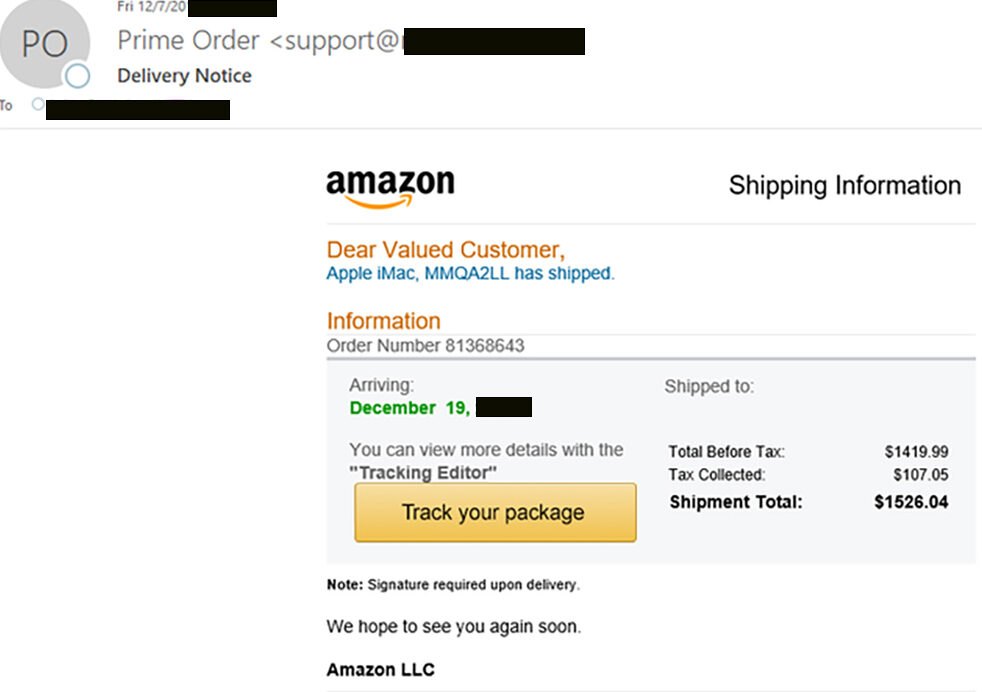
Unfamiliar Transactions and Payment Confirmation Messages are another form of DSD. These messages typically masquerade as payment confirmations for online purchases or receipts from unauthorized purchases that require your attention. If you receive a message regarding a transaction you do not recognize, it might be a fraudulent purchase attempt. You should immediately contact your financial institution and alert them of the suspicious activity. Only provide your debit or credit card information through secure and trusted sites.
Some common types of unfamiliar transaction emails that users may receive include notifications about unauthorized purchases, payment slips for purchases they did not make, and confirmation emails for never initiated purchases. These emails often have suspicious links that, when clicked, can lead to websites that steal credit card information and login credentials or install malware on the user’s device.
Payment confirmation messages used in these attacks often share common characteristics. They may include incorrect details like transaction amounts, product descriptions, or even the recipient’s name. They may feature suspicious links or email addresses, grammatical errors, poor formatting, or unusual time stamps.
To minimize the risk of falling victim to such an attack, users should be vigilant, look for signs of suspicious activity, and do the following:
- Check if you have made any recent online purchases that could correlate with the message.
- Contact the retailer directly using their official website or phone number.
- Avoid clicking on any links within the message or downloading any attachments.
- Double-check for incorrect details or formatting errors that might indicate a fraudulent message.
Email Bombers
Email bombers are a type of DSD that involves sending out many spam emails to a particular email address in a short period. This type of attack overwhelms the recipient, making it difficult to differentiate between legitimate and malicious emails.
Email bombers can also be part of a larger cyberattack, such as distributed denial-of-service (DDoS) attacks or malware campaigns. In these cases, the spam emails mask other malicious activities such as phishing attempts or malware downloads. The sheer volume of emails makes it difficult for victims to identify suspicious activity, allowing attackers to bypass security measures and launch their attacks successfully.
To protect against email bombers, users should ensure that strong anti-spam filters are enabled on their email accounts. These filters can help identify and block malicious messages before they reach the user’s inbox, protecting them from becoming a victim of an email bomber attack. It is also important for users to regularly review their security settings and enable two-factor authentication whenever possible. This additional layer of security can prevent unauthorized access by requiring two different authentication methods before granting access.
Characteristics of Distributed Spam Distractions
Distributed spam distraction is an attack that aims to inundate a victim’s email inbox with a ton of messages, making it difficult to identify and respond to authentic messages. This covert approach can disrupt day-to-day operations and potentially harm financial and personal accounts.
Email Address Targeting
Email Address Targeting is a crucial element of Distributed Spam Distraction, an attack to fill an individual’s email inbox with spam messages. With Email Address Targeting, malicious actors specifically focus on an individual’s email address, flooding their inbox with spam messages to overwhelm them.
Email address targeting is usually the initial step of a larger spam distraction attack. Attackers may combine email address targeting with other tactics to create more significant damage. These spam messages can contain dangerous links or malware, resulting in unauthorized purchases, fraudulent transactions, or even illegal activities. Spam messages can also incorporate unsolicited emails or email bombs that can instigate a denial of service attack, thus leading to more severe consequences.
Most people are susceptible to email address targeting. Individuals who make online purchases, use their debit or credit cards for financial transactions, or use their email for day-to-day operations are more likely to be targeted. Therefore, it’s essential to take proactive measures to protect your email address from email address targeting.
- Enable robust features like multifactor authentication to protect your email address from email address targeting.
- Avoid disclosing your email address online carelessly.
- Prioritize reading only authentic messages from your favorite email sender and mark any suspicious activity and/or links as spam.
- Do not respond or click on any unfamiliar transactions, payment confirmation messages, random excerpts, or nonsensical emails in your inbox.
By being mindful of email address targeting and taking proactive and protective measures, you can avoid falling victim to this attack.
Random Excerpts from Authentic Messages
In the world of distributed spam distraction, a newer technique gaining popularity among malicious actors is using random excerpts from authentic messages. Instead of sending nonsensical emails or traditional spam, these attackers use bits and pieces of genuine emails to create a sense of legitimacy.
Using these random excerpts, the emails can slip past email filters that typically look for keywords and phrases associated with spam messages. Instead of raising red flags, these emails appear innocent and can trick users into engaging with them.
This is why users must be aware of the dangers of suspicious links and attachments. It’s essential to verify the authenticity of any email before taking any action. Check the sender’s details, inspect any links or attachments for anomalous characteristics, and avoid clicking unless you are sure they are legitimate.

Quick Succession of Emails
A quick succession of emails is a common type of distributed spam distraction attack. Attackers use this approach to send a deluge of messages to an individual’s email inbox, quickly overwhelming them with thousands of emails. The sheer volume of these unsolicited messages can lead to missing and ignoring important emails, making it difficult for individuals to keep up with day-to-day operations.
DSD attacks can have detrimental effects on individuals and organizations, including denial of service attacks and email bombs. Denial of Service attacks occurs when an attacker floods an individual’s inbox with so many emails that their email service becomes temporarily disabled. On the other hand, email bombs involve sending large files or messages that cause the recipient’s email storage to become full, leading to the inability to receive new messages.
To prevent falling prey to these spam distraction attacks, you can employ several prevention strategies.
- Use spam filters to detect and block suspicious messages from entering your inbox.
- Implement multifactor authentication, which adds an extra layer of protection by requiring additional login credentials.
- Set up email alerts for unfamiliar transactions or suspicious activity to stay ahead of spam distraction attempts.
This way, you’ll be notified if any unauthorized purchases or payments are being made on your behalf, allowing you to act fast to prevent further damage.

Effects of Distributed Spam Distraction and Prevention Strategies
Distributed Spam Distractions can be a nightmare for users. This type of spam attack involves many unsolicited messages flooding a user’s email inbox, significantly distracting from day-to-day operations.
One potential side effect of DSD is the overwhelming volume of messages that can quickly become impossible to manage. Users may receive dozens, if not thousands, of spam emails daily. These messages can also contain random excerpts and suspicious links, making it harder for users to distinguish authentic messages from those sent by malicious actors.
Users can employ several prevention strategies to prevent DSDs from causing harm. One popular method is to use multifactor authentication for email accounts. This adds an extra layer of security, making it harder for attackers to access users’ email addresses and credit card details.
Another strategy is to make use of robust features in spam filters. This can help to combat the sheer volume of email bombs and confirmation emails that may be sent in quick succession. Spam filters can be set up to automatically move messages to spam folders, preventing them from cluttering up users’ email inboxes.
Wrapping Up
Distributed Spam Distraction emails are on the rise again, and they can be especially damaging for users unaware of the risks. It’s essential to remain vigilant and to take measures such as enabling multifactor authentication and robust spam filtering services to protect yourself from malicious actors. Remember that it’s better to be safe than sorry, so if anything appears suspicious, only click on links or open attachments once you have verified their authenticity. If you receive an email you need clarification on, you can send it to us, and we will check it out.