Working from home is the current daily routine for many. Unfortunately, the security of a home office is often less than stellar compared to in-office security. We could have come up with some boring basic cybersecurity tips, but we wanted to do something special. We have developed our top six cybersecurity tips to add security to your home office. Let’s dive in!!
Table of Contents
1. Secure Your Internet Connection

Cybersecurity tip number 1 might seem like a no-brainer, but you’d be surprised how often we see unsecured connections.
Larger companies usually employ IT specialists responsible for the company’s cybersecurity. This includes protecting your Internet access and the corporate cloud against external attacks. However, as soon as you leave the office, you leave some safe ground in this regard. That’s why cybersecurity tip number one is crucial to keeping your network secure.
You must be careful with third-party WLAN networks and computers if you work outside the office. Hackers could use special software or inadequately secured applications to place themselves between you and the relevant server to read or manipulate your communications. This way, they gain access to the company’s IT and sensitive data. Such incidents are referred to as man-in-the-middle attacks.
2. Activate Your Firewall

Cybersecurity tip numero dos, turn on your firewall. I’m unsure how or why so many people use their computers without their firewalls turned on, but it’s not safe, so don’t do it.
Activate your firewall in the security settings of your computer. Be careful with WLAN networks that are not secured! Turn off the function to automatically connect to open WLAN networks. Instead, use mobile data and surf with your laptop via a mobile hotspot or virtual private network (VPN) if your company provides one.
2A. What is a Firewall?
A firewall monitors incoming and outgoing network traffic and allows or blocks data packets based on security rules. It provides a barrier between your internal network and incoming traffic from external sources (such as the Internet). In this way, the built-in filtering mechanism manages network traffic and prevents attacks from the outside.
2B. Windows 10 Firewall Configuration
Open the Start menu and type “Windows Defender Security Center” in the search bar. Click on the tab/tab “Firewall & Network Protection.” You will be offered the choice of “Domain Network,” “Private Network,” or “Public Network.” Please select all of them accordingly and enable the firewall by flipping the button in each case.
2C. Firewall Configuration Mac OS X 10.5 and Newer
Select “System Preferences” from the Apple menu and click the “Security” tab. Click on the “Firewall” tab and select the mode used for the firewall. Important note: Firewall activation must be done manually on Apple devices; it is not part of the basic settings.
3. Know the Dangers of Using Private Endpoints

Cybersecurity tip number 3, make sure that all devices you are connecting to your work network are adequately secured.
Shadow IT refers to programs, services, or personal devices that employees use in connection with company data without prior coordination.
In the current situation, where many employees have been forced to work from home without much-advanced planning, there is a high risk that employees will access the corporate cloud from their private computers to continue their work.
Any unknown device or program poses a potential security risk to corporate data. If those in charge don’t know of its existence, they can’t take the necessary security- or privacy-related precautions. Do not process company data on personal end devices. If it is unavoidable given the current situation, have this use approved in advance or equip the device with the necessary software for secure working.
4. Use Private Devices Securely

Cybersecurity tip number 4 is similar to cybersecurity tip number 3. Ensure all your devices are secured because you don’t want to be the reason your company gets hacked.
Avoid if possible: Yes, you have a work computer, but the monitor on your notebook is more prominent, the processor is faster, and you still have a graphics program installed there that you like to use, so you prefer to work on your device. Stop. Even if it’s tempting, if you have appropriate company devices or access gates (e.g., Citrix, Microsoft Terminal Server), always use them for business activities, not your personal ones.
Obtain permission: Never use endpoints without consent from your supervisor and your company’s IT managers. Otherwise, you may not only be in breach of your employment contract but may even be liable for any damages incurred.
5. DSGVO-Compliant Home Office

Cybersecurity tip number 5 is to make sure you comply with any rules or regulations you must adhere to.
Data protection remains a significant issue even if you work away from your office. Although the General Data Protection Regulation (GDPR) does not contain specific home office regulations, your obligations remain. Accordingly, it is crucial to avoid potential threats to the confidentiality, integrity, and availability of personal data processed from home by taking appropriate technical and organizational measures (so-called TOMs).
In addition to the measures already mentioned, it is advisable to issue a so-called additional guideline for working from home – however, this is not mandatory. Existing IT company agreements are also valid in the home office!
6. Stay Alert & Be Aware of Phishing Scams
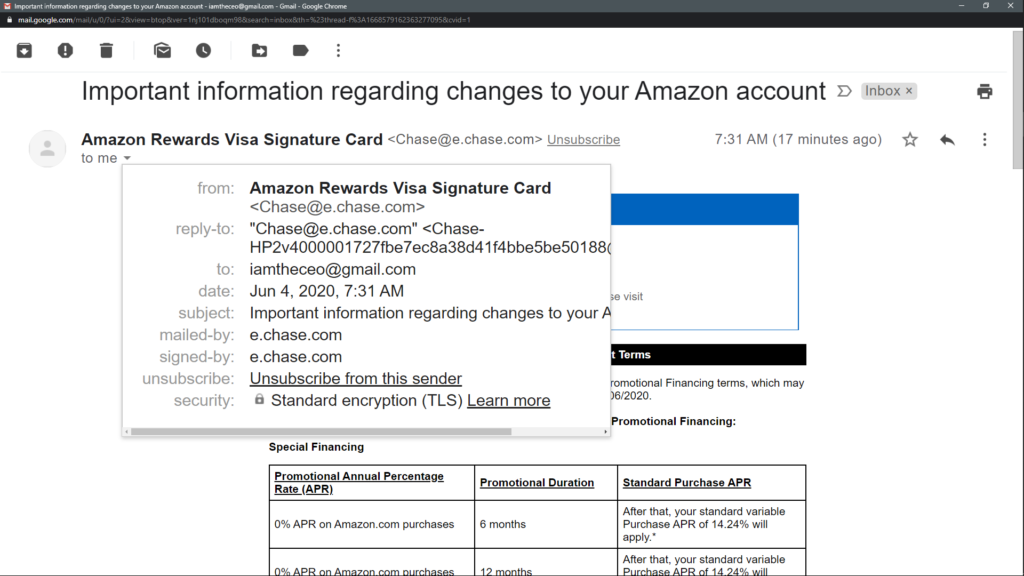
The final and probably the most critical cybersecurity tip is staying aware and being on the lookout for phishing emails. We have started using a program called IronScales to report phishing emails, and it’s borderline amazing. So maybe IronScales should be cybersecurity tip number seven?
Criminal hackers cleverly exploit special situations to trick their victims and obtain their data. Therefore, be especially attentive if you receive emails from unknown persons about current events or if you are asked to perform a specific action. Criminals often impersonate colleagues and superiors (CEO fraud). Consequently, pay attention to warning signs in writing style and communication type. Contact the colleague via a second communication channel to verify the authenticity of his message.
Install updates, and cross-check questionable content and prompts! Phishing, and especially CEO fraud, are not necessarily technical attacks. Be wary of emails from unknown persons if they ask you to perform a specific action, such as installing a program, handing over information, or transferring a sum of money. Be aware of their internal communication processes, which also apply in the home office!
6A. When Superiors Are In a Hurry…
To prevent CEO fraud attacks, you should pay particular attention to your superiors’ writing and communication styles. Does your boss suddenly call you by your first name, even though they are usually on a first-name basis? Does he use an unusual greeting? Does he typically write extensively but now only very briefly? All these can be warning signals. And if in doubt: contact the colleague via another communication channel to check the message’s authenticity – better once too much than too little.
6B. How Do I Unmask the Fake Business?
Writing style: everyone has their writing style. If there are deviations here, you should pay attention. Does your boss greet you with Hey or what’s up? Does he always use certain idioms or phrases? Does he have a unique signature? Maybe it usually says “sent from my cell phone” under the messages, but now it says “sent from my iPhone,” even though your boss is a big Android fan.
Communication channels: If your boss always communicates by email but now suddenly sends you important instructions via Whatsapp, his cell phone could have been hijacked by SIM swapping. Especially in emergencies, you should agree on binding communication channels and processes. If these are not adhered to, you should ask.
Inquiries not possible: If the boss sends you an important instruction and indicates that he is not available for questions, this puts you in a difficult situation. Due to remote work in the home office, it is often unclear which appointments and obligations are pending or which decisions have been made. Especially in the current situation, there should be transparency about who is unavailable and when.
Managers also have a responsibility here: Ensure transparency, transparent processes, and secure communication channels so that employees can constantly reassure themselves, especially when making important, far-reaching decisions.
We’ll leave you with one last cybersecurity tip. That is to stay diligent, keep on top of security trends, and if you ever receive a suspicious email, do not click on it and do not input your credentials. Stay safe out there!

