Every business needs a robust network security system to protect its sensitive data. There are numerous ways to protect your network and data from outside threats. Some network security service providers (NSSPs) focus exclusively on endpoint security; others give security a high priority and compensate for any shortcomings in server-side security by providing security as a service (SaaS). Sometimes the line between a SaaS and an NSSP is blurred. For example, some organizations buy services from network security services providers and then pay an additional fee to have an NSSP provide security as a service to their network.
Table of Contents
What is a Network Security Service Provider?
A network security service provider provides computer or information technology-related products and services that help businesses secure networks against attacks such as viruses, worms, spyware, spam, phishing, denial of service, malware, hacking, unauthorized access, identity theft, intellectual property loss, etc. The term “security” can be used interchangeably with “protection,” but there’s no need to confuse the two terms because they mean different things. In this article, we’ll use the word “security” to refer specifically to protection from malicious software and other cyberattacks.
How to Find Competent Network Security Service Providers?
Before choosing to meet with any network security service providers, you should first determine what kind of threats you’re most concerned about. You might choose a product that protects computers at endpoints like desktops and laptops to prevent hackers from stealing confidential company documents. On the other hand, if you want to stop employees from accessing corporate email accounts without authorization, you may prefer a solution that secures servers and applications inside firewalls.
You also must consider whether you want to purchase a standalone product or subscribe to a managed service. A standalone product typically requires more technical expertise than a subscription service does. However, many companies opt for a hybrid approach combining both methods. This allows them to get the best value out of each type of product while minimizing costs.
The second thing you should consider is who will manage your network security solutions. Will you hire someone else to install and maintain your network security systems? Or will you work directly with a vendor? There are pros and cons to either option. Working with a third party means you don’t have direct control over the implementation process. But working with a third party often leads to better pricing since vendors know exactly which customers require certain features and capabilities. It also helps ensure that all aspects of the project meet industry standards. Finally, having network security service providers handle installation and maintenance ensures that everything goes smoothly during the transition period.
You should also ask yourself how much time you can devote to managing your network security solutions. Are you willing to spend hours monitoring logs, responding to alerts, troubleshooting problems, and updating patches every month? Or would you rather let a professional do these tasks so you can concentrate on growing your business?
Finally, ensure you understand the scope of the contract you sign with your chosen network security service provider. Some contracts include only one aspect of your overall IT infrastructure. In contrast, others cover multiple areas, including desktop support, server management, application delivery, data backup, disaster recovery, and even wireless networking. Make sure you fully comprehend the details of any agreement you reach with a potential partner. Otherwise, you could pay extra fees later when unexpected issues arise.
What is the Difference Between MSP and MSSP?

MSP stands for Managed Service Provider, while MSSP refers to Managed Security Service Providers. Both refer to organizations that offer IT support services such as computer maintenance, virus protection, backup, etc. Still, one provides those services through a traditional sales channel, whereas the other sells them exclusively online. In addition, some MSPs specialize in providing only certain kinds of services, like antivirus or firewall software. Others focus primarily on hardware installation and configuration. Some even offer consulting services.
The key distinction between the two models lies in how much management work the provider performs. An MSP will handle all aspects of your technology needs except perhaps installing new devices. On the other hand, an MSSP will take care of everything, including a cloud security plan, vulnerability management, cybersecurity penetration testing services, digital risk & threat monitoring, compliance monitoring, and firewall management.
What is Network Security As a Service?

Network security as a service refers to several ways an organization purchases its network security tools and outsources its management. NSAS include:
- Managed Security Services – An MSS involves outsourcing some or all of the duties associated with maintaining a firewall, antivirus program, intrusion detection system, anti-spam filter, web content filtering, URL blocking, email gateway, VPN server, proxy server, and other similar functions. These responsibilities usually include installing and configuring hardware and software components, patching vulnerabilities, creating policies, training users, and providing ongoing support. The benefits of this model include reduced capital expenditures and operating expenses, increased flexibility, improved scalability, and greater efficiency.
- Cloud Security Service Providers – Cloud services provide remote access to computing resources through virtualized networks. They allow organizations to use cloud technology to store data, run programs, and perform online transactions. In addition, cloud security services offer additional protection by allowing administrators to monitor activity remotely within the cloud environment. Some cloud security products enable organizations to create private clouds using public infrastructure, such as Amazon Web Services.
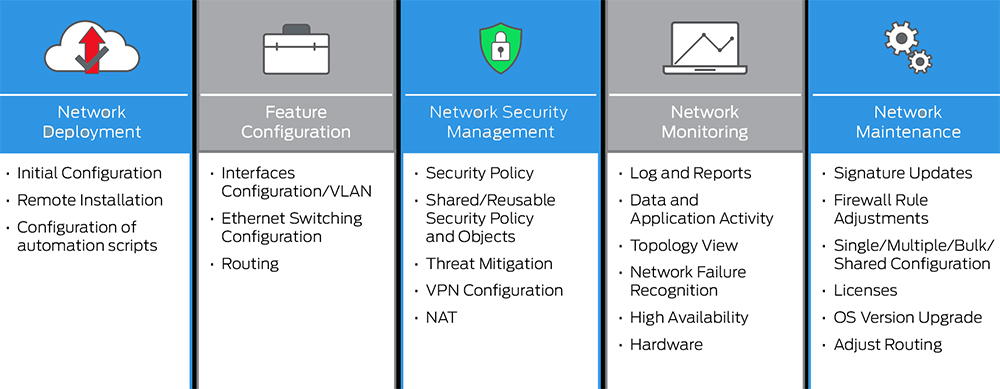
- Security Management Software – Network security management software automates various administrative processes related to securing computer networks. For example, IT staff members can centrally configure devices, set up user groups, deploy new technologies, track usage statistics, and generate reports.
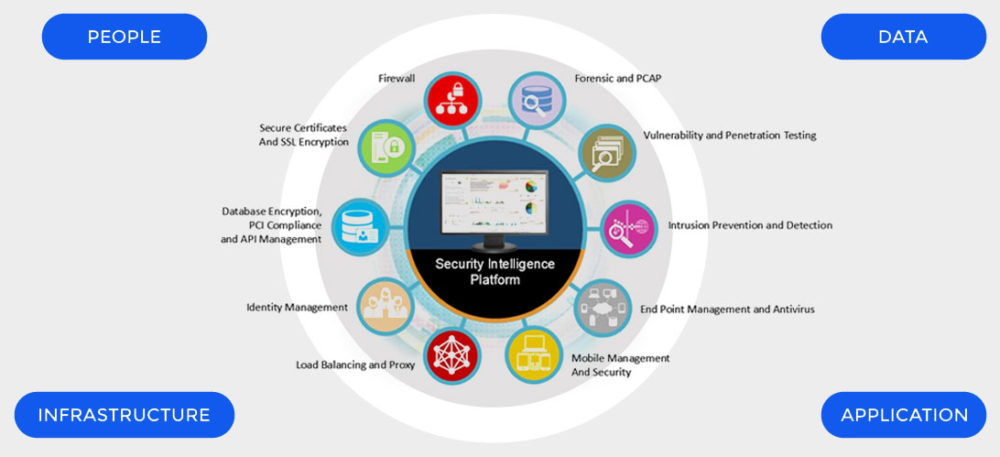
Security Audits, Vulnerability Assessments, Penetration Testing, and Threat Intelligence
A security audit is performed when a company wants to determine if its current security measures are sufficient for protecting against potential threats. A vulnerability assessment is used to identify weaknesses in existing security controls. This analysis typically includes identifying known exploits, weak passwords, default accounts, outdated applications, etc. Penetration testing determines what information an attacker could gain from unauthorized access to a particular resource. Finally, threat intelligence provides companies with real-time updates about emerging cyber threats that may be targeted at their specific industry sector. It helps businesses stay ahead of hackers by giving them insight into malicious activities targeting their industries.
How Does a Managed Security Solution Work?
To protect your business’s sensitive information, you need strong firewalls, virus scanners, spam filters, password managers, etc. However, these systems can only do so much without human intervention. Managers must constantly update and maintain each component, ensuring it runs correctly. There’s no way to know if something goes wrong until someone notices a problem. That means downtime costs money while employees spend time troubleshooting issues instead of doing productive tasks.
With a managed security solution, however, everything runs automatically. You don’t have to worry about updating patches, managing servers, monitoring logs, or any other aspect of network administration. Instead, you focus on growing your business and leaving the rest to experts specializing in those areas.
Why Should You Consider a Managed Security Solution Over DIY Solutions?
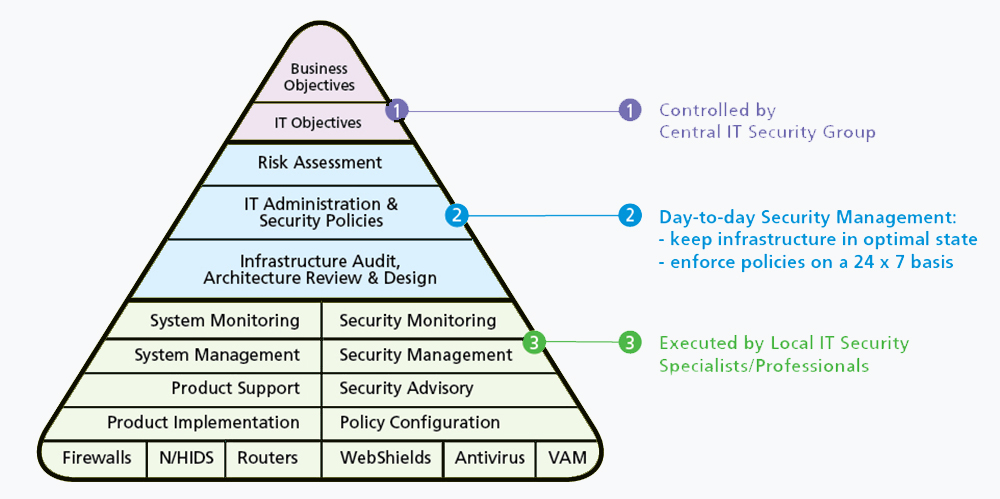
Managed security solutions give you more control than DIY options because they automate many aspects of network operations. These tools also help reduce operational expenses by eliminating manual labor. Plus, they ensure all components are working correctly before anything else happens. With DIY solutions, you might not notice problems until after they’ve already occurred. The result: downtime, lost productivity, and wasted money. Is a managed security solution right for me?
A managed security solution makes sense if you want to take advantage of the latest technology but aren’t ready to commit full-time resources to maintain your infrastructure. They provide comprehensive protection across multiple layers of defense, including antivirus scanning, firewall configuration, intrusion detection/prevention, web application filtering, email encryption, data loss prevention, anti-spam, content screening, and more. In addition, most offer 24×7 support via phone, chat, ticketing system, or remote desktop connection.
What Types of Services Does a Managed Security Provider Offer?
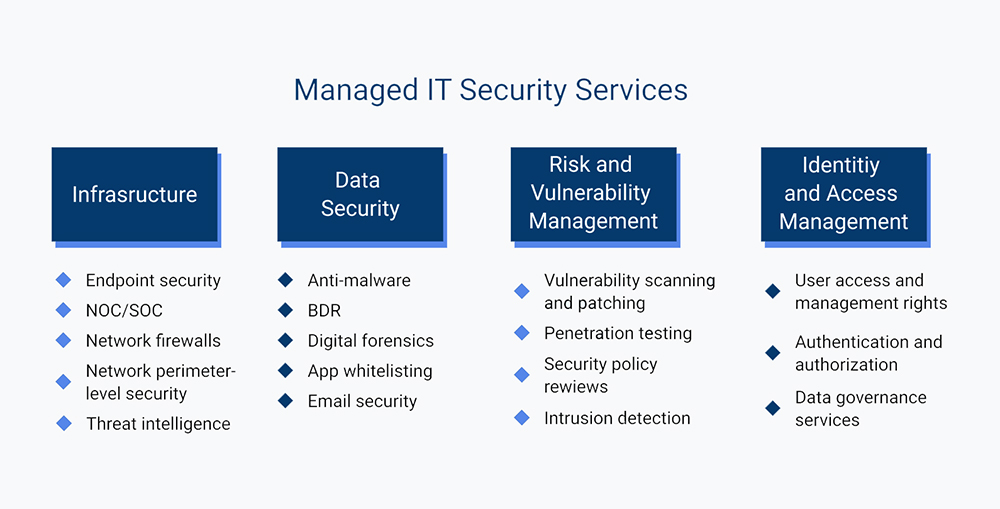
Most managed security providers offer a wide range of services that should include many, if not all, of the following:
- Antivirus & Antispyware Protection – Most vendors include basic malware scans as part of their monthly subscription fee. Some go one step further and scan files locally rather than just checking emails. Others even use artificial intelligence to detect new viruses faster than humans ever could.
- Firewall Management – Many MSPs will configure your firewall settings based on your organization’s needs. For example, you might set up port forwarding rules to allow certain apps through your corporate firewall. Or maybe you’d like to block unwanted traffic altogether. Either way, it’s essential to keep things secure.
- Intrusion Detection/Prevention – When a hacker tries to break into your computer, he’ll often try different methods to get past your defenses. Intrusion detection software looks at suspicious activity and alerts IT staff when an attack is detected. This helps prevent breaches from happening in the first place.
- Web Application Filtering – Web applications such as websites, online banking portals, eCommerce sites, social media platforms, etc., pose unique threats that require special attention. A well-managed security vendor will monitor them regularly and alert administrators if malicious code is found.
Without proper training, it can be difficult to tell whether something is legitimate or harmful. That’s where web application filters come in handy. By blocking known bad actors, these programs protect against phishing scams, identity theft, spamming, click fraud, and much more.
- Email Encryption – Email has become a significant vector for hackers looking to steal sensitive information. If someone sends you an attachment with a virus, ransomware, spyware, or other types of malware embedded within it, there’s no telling what damage it may cause. Many companies encrypt messages using PGP or S/MIME standards to avoid this risk.
- Data Loss Prevention – Data loss prevention systems look for inappropriate file attachments, URLs, keywords, metadata, and other indicators of potential privacy violations. These tools help ensure that confidential documents are only shared among authorized users.
- Anti-Spam – Spammers have gotten very sophisticated over time. As they’ve learned how to game existing technologies, spammers have developed ways to bypass traditional techniques used by ISPs and firewalls. Anti-spam solutions work around those loopholes to stop unsolicited bulk mail before it reaches inboxes.
- Content Screening – Content screening prevents employees from viewing potentially offensive material while working remotely. The technology works by scanning content for keywords associated with pornography, violence, hate speech, and so forth. Once flagged, the system automatically blocks access to the offending page.
- Network Security Monitoring – NSMs provide real-time visibility into network activities. They can identify attacks quickly because they don’t rely solely on signatures. Instead, they analyze data packets and correlate events across multiple devices.
- Malicious Software Removal Tool – MSRT provides automated removal capabilities for various types of viruses, worms, Trojans, rootkits, adware, and other forms of malware. Administrators run the tool and let it do its thing.
- Remote Access Control – RAC allows remote workers to connect their computers directly to company networks via VPN connections. With this feature enabled, employees can securely log onto servers and perform tasks without worrying about being hacked.
How Does Network Security As a Service Differ From Managed Security Services?
NSAS differs from MSSPs because they involve different levels of involvement. With an MSS, the customer retains full ownership of their network security solution but delegates responsibility for day-to-day operations to a third party. This may be done via a subscription agreement where the customer pays monthly fees based on the number of computers connected to the Internet. Alternatively, customers may pay per incident basis when a problem occurs.
With NSAS, however, the vendor assumes complete control over the entire process. It installs and maintains the equipment, monitors performance, creates policy settings, provides technical assistance, and responds to incidents. Customers are typically charged hourly rates that vary depending on the expertise required.
What Types of Companies Benefit From a Network Security As a Service Model?

Image by David Mark from Pixabay
Companies with large numbers of employees who need constant connectivity to business applications can significantly benefit from NSAS. Large enterprises often require multiple layers of firewalls between internal systems and external connections. A single point of failure could cause significant damage if the connection is lost. By purchasing NSAS, these businesses gain more efficient administration while reducing costs. Smaller firms also find value in NSAS since many vendors now sell affordable solutions for small businesses.
Conclusion
We hope that this article clears up any questions you may have had regarding network security service providers. If you’re looking for a local security team to improve your network infrastructure, beef up your cybersecurity solutions, and help keep cyber threats at bay, please send us a message or comment below.





Recent Comments