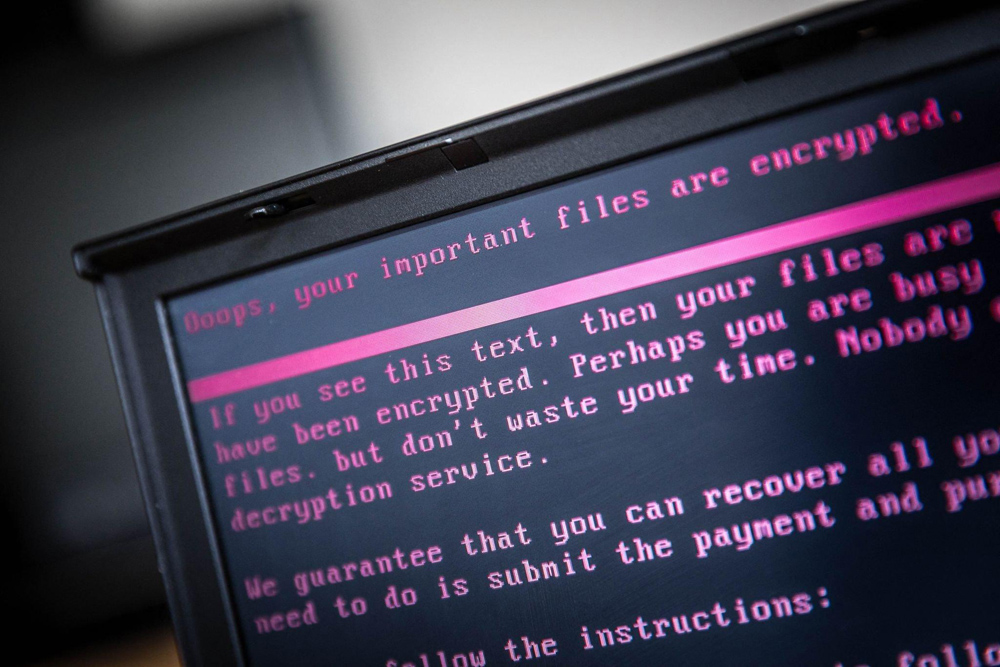
Ransomware is a cyber threat everyone should worry about because it has affected millions of individuals and organizations across the globe over the last few years. It is a form of malware that encrypts a victim’s files and demands a ransom payment be made in exchange for the decryption key. While ransomware attacks have been around for quite some time, they have become increasingly prevalent and sophisticated, making them harder to detect and prevent. In this blog, we’ll discuss whether paying the ransom is a good business decision, and take a a closer look at the pros and cons of ransomware payments.

Table of Contents
Should You Pay Ransomware Ransom? Reasons For and Against
The decision to pay or not to pay is challenging, and it requires careful consideration of each option’s potential risks and benefits.
Reasons for Paying Ransom Demands
While paying the ransom may not be an ideal solution to a ransomware attack, businesses may choose to do so. Here are a few reasons why they might:
1. Obtaining Decryption Keys: In some cases, paying the ransom may be the only way to get the decryption key needed to unlock a company’s encrypted data. With the decryption key, the data may be recovered forever, which could be catastrophic for some businesses.
2. Preventing Data Loss or Leaks: If the hackers have threatened to leak a company’s data to the public or sell it on the dark web, paying the ransom may be the only way to prevent a data breach and the subsequent damage to the company’s reputation.
3. Saving Time and Resources: Recovering from a ransomware attack can be time-consuming and costly. Paying the ransom may save a company time and resources that would otherwise be spent on rebuilding systems and restoring data.
Reasons for Not Paying Ransom Demands
While there are some reasons why businesses may choose to pay a ransom demand, there are also reasons why they may decide not to. Here are a few:
1. Funding Criminal Activities: Paying the ransom funds criminal activities, and that’s a big no-no. It encourages them to continue their illegal actions and target other companies.
2. Setting a Dangerous Precedent: If businesses continue to pay ransoms, it will only encourage more hackers to engage in ransomware attacks because they know they can profit from it. This sets a dangerous precedent and puts all businesses at risk.
3. Legal Consequences: Paying ransoms may also result in legal consequences, as some ransoms may be illegal under US law. The Office of Foreign Assets Control (OFAC) has advised that paying ransoms to individuals or entities on its sanctions list may result in civil penalties or other strict liability.
The Decision-Making Process
The decision to pay or not to pay a ransom demand should not be taken lightly. Before making a decision, businesses should ask themselves the following questions:
1. How critical is the data that has been encrypted? Can we function without it, or is it essential to our operations?
2. Have we exhausted all other options for recovery, such as using decryption tools or contacting law enforcement agencies?
3. Do we have cyber insurance? Will the insurance company cover the cost of paying the ransom?
4. What are the potential consequences of paying or not paying the ransom on our business, industry, and customers?
Alternatives to Paying Ransom Demands
Before deciding to pay a ransom demand, businesses should consider some alternatives. Here are a few:
1. Use Decryption Tools: Many decryption tools can be used to recover data encrypted by ransomware. Some of these tools are free, while others are paid. Businesses should explore all options before resorting to paying a ransom.
2. Contact Law Enforcement: Law enforcement agencies may be able to help recover data without paying a ransom. While it may take longer, it is a safer and more legal option for businesses.
3. Enhance Security Practices: Businesses should use ransomware attacks as an opportunity to review and enhance their security practices. This includes implementing backup solutions, using file sharing and operating systems with the latest security patches, training employees on security best practices, and having a plan to respond to cyber threats.

Financial Considerations
Ransomware attacks can wreak havoc on a business, causing data loss, reputational damage, and financial losses. Some companies may feel compelled to pay ransom demands to get their data back in such situations. However, making a hasty decision without considering the legal and financial implications can have serious consequences.
Cost of Payment
As touched on above, the decision to pay a ransom is not easy, as it is laden with financial considerations that may significantly impact the victim organization’s future financial health.
Ransom demand
One of the primary financial considerations when deciding whether to pay a ransom is the amount demanded. Ransom demands can range from a few thousand dollars to millions, depending on the victim’s perceived ability to pay. For small businesses, a ransom demand that amounts to weeks, if not months, of revenue, could easily cripple their operations.
Legal fees and sanctions
Another cost that victims of ransomware should consider is the potential legal fees and sanctions that may be incurred due to paying the ransom. Organizations may sometimes face penalties for engaging in illegal activities if the payment is made to a sanctioned organization or individual. It is wise for victims to consider the long-term ramifications of these factors when deciding whether to pay the ransom or not.
Likelihood of future attacks
One of the most difficult considerations when evaluating whether to pay a ransom is the likelihood of future attacks. Unfortunately, paying the ransom can signal to cyber criminals that the victim is a soft target, making them more likely to be targeted. This puts the victim in a catch-22 situation where paying the ransom could lead to more ransom demands in the future.
Financial impact
When weighing the cost of paying a ransom against the consequences of not paying, organizations must consider the potential overall financial impact. On the one hand, paying the ransom may bring the immediate crisis to a close. Still, on the other hand, it can leave a significant dent in the company’s finances, causing many issues down the line. For instance, if the organization decides to pay the ransom, it may have to offset the cost by reducing expenditures, laying off employees, or scaling back its operations for a certain period.

Risk of Not Paying
Ransomware attacks are among the most prevalent cyber threats in the digital age. In 2022 alone, ransomware attacks resulted in damages worth billions of dollars. One of the primary issues victims of such attacks face is whether to pay the ransom. While paying the ransom may seem like the easiest way out, there are risks associated with giving in to the ransomware operators. However, the decision not to pay a ransom demand also comes with its own set of pitfalls.
Permanent Data Loss
One of the significant reasons for paying a ransom is to regain access to encrypted files. In some cases, the decryption tools to recover the encrypted data may not be available, making it impossible to retrieve the files without paying the ransom. If the victim refuses to pay, they risk losing the data permanently. Losing valuable information, such as business processes, sensitive financials, or customers’ data, can have far-reaching consequences and even lead to the organization’s closure.
Business Disruption
Not paying the ransom can create significant disruption or halt business operations. For example, if the ransomware attack affects the organization’s computer systems, it may hamper the ability to perform vital functions. Suppose the victim does not have a reliable backup system. In that case, the organization may struggle for an extended period resulting in lost productivity, revenue, customer base, and more.
Legal Penalties
Sometimes, paying a ransom may not be the most legal decision as it could breach sanctions or regulations. However, not paying can also result in legal penalties. Organizations operating in heavily regulated sectors are at high risk of legal or regulatory enforcement action. Not only would an organization face potential litigation costs, but criminal proceedings and hefty fines could also be imposed.
Reputation Loss
The consequences of a ransomware attack often lead to reputational damage. Customers will likely lose confidence in an organization that is either unpaid or reduced to paying a ransom demand. Moreover, if the data is compromised, the information breaches can lead to adverse publicity, exposing the organization and its shareholders. The more sensitive the data, the more the reputational damage.
Stolen Data
Threat actors may resort to publishing or selling the stolen data if the victim refuses to pay a ransom. Suppose sensitive information related to a client or customer is exposed. This can lead to reputational damage, litigation, and regulatory or legal penalties. In some cases, this damage to individuals can have far-reaching consequences, such as identity theft.

Security Practices to Prevent Future Attacks
While it may be tempting to pay the ransom and regain access to your data, there are several considerations to remember. This article will focus on security practices businesses can implement to prevent future attacks. We’ll cover everything from employee training to software updates, so let’s dive in and get started.
Employee Training
One of the most important steps businesses can take to prevent future ransomware attacks is to invest in employee training. Employees are often the first line of defense against cyber attacks. They must be aware of the risks associated with clicking on suspicious links or opening attachments from unknown sources. Some key things to cover in employee training include:
- How to identify suspicious emails or messages
- Best practices for creating strong passwords
- What to do if they suspect a ransomware attack
- How to properly handle sensitive information
Effective Training Methods for Cybersecurity
Businesses can use various training methods and tools to educate their employees about cybersecurity.
– Simulated phishing attacks: One effective method involves performing simulated phishing attacks to determine how vulnerable employees are to social engineering attacks. This helps identify areas where employees may need more training and help reinforce good security habits.
– Interactive cybersecurity courses: Another effective method is interactive cybersecurity courses that provide engaging and practical scenarios for employees to learn from. These courses can cover a wide range of topics, from identifying potential threats to handling sensitive data, and can be tailored to meet the specific needs of different departments within an organization.
– Regular Security Updates: It is also necessary to ensure that employees understand the importance of regular security updates and their role in protecting against cyber threats. This includes updating operating systems, software, and anti-virus programs to ensure the latest security patches and protocols are in place.
Reinforcing Good Security Habits
Providing employee training is only the first step in protecting against cyber threats. It is equally important to reinforce good security habits to ensure that employees remain vigilant, stay up-to-date with the latest security protocols, and proactively identify potential threats.
– Continuous Education: The landscape of cyber threats is constantly changing, so it is crucial to ensure that employees receive continuous education and training on the latest developments.
– Enforce Password Policies: Employees should be trained to use strong passwords, avoid sharing them, and update them regularly. Additionally, enforcing multi-factor authentication can go a long way in securing systems and data.
– Avoid Downloading Unknown Files: Employees should be warned against downloading files from unknown sources or clicking suspicious email links. This can prevent them from inadvertently downloading malicious software or accidentally exposing the company to a ransomware attack.
– Encourage Reporting: Employees should be encouraged to report any suspicious activities immediately. By doing so, timely action can be taken, and the threat can be contained before it escalates.
Regularly Update Software
Another essential security practice is to update all software programs regularly. Not only does this help prevent attacks, but it also ensures that vulnerabilities are patched as soon as they are discovered. It’s important to remember that cybercriminals are always looking for ways to exploit out-of-date software and operating systems. You can stay one step ahead of potential attackers by keeping everything up-to-date.
Data Backup
Data backup is another crucial security practice that can help businesses avoid paying a ransom in the event of an attack. Regularly backing up your data to a secure location (either on-site or off-site) ensures you always have a clean copy of your files. This makes restoring your systems easier and avoids paying a ransom to regain access to your data.
Network Segmentation
Network segmentation is breaking up your network into smaller, more secure segments. By doing so, you can limit the damage caused by an attack. For example, suppose an attacker gains access to one part of your network. In that case, they may be unable to access other areas containing sensitive data or essential systems.
Use Antivirus and Anti-Malware
Antivirus and anti-malware software are essential tools in the fight against cyber attacks. They can detect and prevent malicious software from infecting your systems, and many even include features like email scanning and firewalls. Always keep these programs up-to-date and consider using multiple layers of protection for added security.
Monitor Your Systems
It’s essential to regularly monitor your systems for any signs of a potential attack. This can include unusual network activity, failed logins, or a sudden increase in file encryption. By monitoring your systems, you can detect potential attacks early on and take steps to prevent them from causing significant damage.
Wrapping Up
When faced with a ransomware attack, businesses may be tempted to pay the ransom to regain access to their data. However, paying the ransom does not guarantee that the attackers will provide the decryption key. It also encourages the growth of cybercriminal activities.
Law enforcement agencies and cybersecurity experts advise businesses not to pay the ransom. Instead, businesses should focus on preventing and mitigating the impact of ransomware attacks. This includes having a solid cybersecurity policy, regular data backups, and a robust recovery plan.
Insurance companies offer cyber insurance policies to cover losses incurred by cyber attacks, including ransomware attacks. Cyber insurance providers may offer additional support and resources, such as access to cybersecurity experts and decryption tools.
In conclusion, paying the ransom in a ransomware attack is not recommended. Businesses should focus on preventative measures and mitigating the impact of the attack. Businesses can significantly reduce the risk of a ransomware attack by having a comprehensive cybersecurity policy, regular employee training, and a strong data backup and recovery plan. In the event of an attack, businesses should contact their IT team, law enforcement agencies, and their insurance company for support and resources.