
by Chad Ostreicher | | Best Practices, Cloud Services, IT infrastructure, IT Services, Security, Tips
We’ve all been there, the time when a computer or network problem arises, and you need to call an expert to help. Unfortunately, this can be a costly proposition. If you are not careful with your money, you may pay more than necessary for their technical support...

by Chad Ostreicher | | Best Practices, Hardware, IT infrastructure, IT Services, Security, Tips
As a proactive network consulting company in Arizona, small to medium-sized businesses want proactive IT solutions. That’s why we don’t wait for problems to arise before solving them. Being proactive with your IT is the best way to ensure you are always...

by Chad Ostreicher | | Best Practices, IT infrastructure, IT Services, Security, Tips
A cyber security assessment is a process that involves assessing what risks exist, what vulnerabilities are present, and what countermeasures are in place to protect against those risks. This process aims to produce an action plan for addressing the risks and...
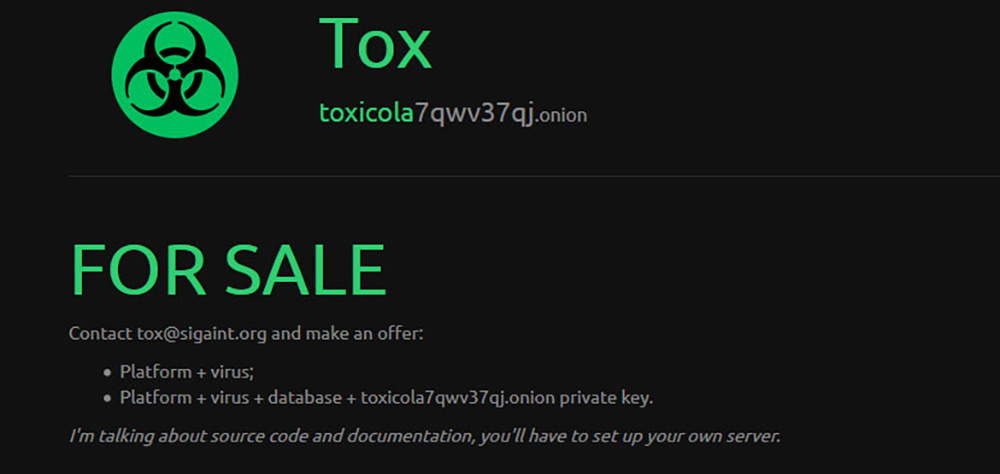
by Chad Ostreicher | | Best Practices, IT infrastructure, IT Services, Ransomware, Security, Software, Tips
You may or may not have heard about this new type of cybercrime called Ransomware as a Service. This is where the bad guys sell their wares to other criminals who want to make money by infecting computers with malware and then demanding payment for them to access...

by Chad Ostreicher | | Best Practices, IT Services, Remote work, Security, Tips
Many types of malware can invade your computer and phone, but one of the most infamous is a keylogger. A keylogger, or keystroke logger, is software that records everything you type on your keyboard and anything you enter in forms, including passwords. This type of...

by Chad Ostreicher | | Best Practices, Cloud Services, IT infrastructure, IT Services, Security, Tips
As the digital era advances, so does the need for security. The threat of hackers and data breach costs are growing every day. You may not be aware, but hackers often target small businesses, and data breaches are happening at an alarming rate. Companies spend more on...








Recent Comments