You may or may not have heard about this new type of cybercrime called Ransomware as a Service. This is where the bad guys sell their wares to other criminals who want to make money by infecting computers with malware and then demanding payment for them to access those infected machines. The problem here is that it’s easy for these crooks to sell you Ransomware because they don’t need any technical skills at all!
Table of Contents
What is Ransomware as a Service?
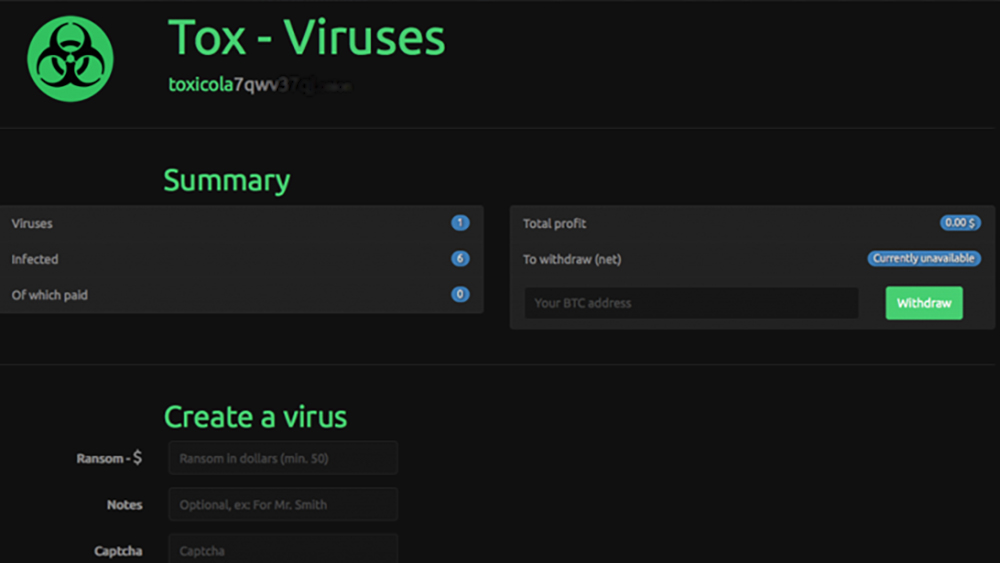
What is Ransomware as a Service, and who uses it? Ransomware as a Service (RaaS) offers ransomware code, usually through an online cybercrime marketplace that allows people to buy and sell Ransomware. The criminals who created the malware can profit from their work by selling shares in the virus, which launches after infecting your system with harmful software. It’s not just the big-name ransomware gangs like REvil, Conti, and Darkside anymore- now it’s available to anyone who wants to create an attack on unsuspecting businesses or individuals.
RaaS started like many other types of Ransomware in the underground forums. What was once just a few people pushing phishing emails with malware and other cyber threats has now evolved into an affiliate model that offers monthly subscriptions. It’s wild! Cybercriminals have created a proven business model and marketplaces to sell and exchange malware that works alongside RaaS software to launch attacks on unsuspecting users.
By pooling resources from other ransomware authors, ransomware operators can create their own custom all-in-one hacking solution to cyber attacks. This means that what used to be a small business-type operation has now turned into an enterprise with tons of money being made for the attackers involved in RaaS.
It is even more dangerous because many hackers have also found ways to get around anti-malware software. So victims will not realize what has happened to their data until it’s too late. This means that what used to be a small-time operation now has the capability of crippling businesses and companies by encrypting their files and locking them out from any access or use on their computers. Ransomware as a service is truly an enterprise with cybercriminals gaining money off of what used to be a smaller cybercrime operation.
Ransomware as a service has allowed ransomware attacks to flourish in recent months, affecting businesses worldwide by encrypting their data while also gaining access to important files that could otherwise affect business operations or customer relations. What used to be a small-time virus only attacking unsuspecting users is now a cybercrime enterprise. This means that what used to be smaller operations have grown into an enterprise capable of crippling businesses by encrypting their data and locking them out from any access or use on their computers, all while gaining money for the attackers involved in RaaS.
How Does Ransomware as a Service Work?
The first step in creating a successful ransomware campaign involves finding victims. Hackers will use social media sites like Facebook or Twitter to find potential targets. Once someone clicks on one of these links, they open up the malicious website containing the link. From there, the site’s hacker will install browser extensions onto the user’s computer. These extensions allow them access to all sorts of information, including browsing history, search terms typed into Google, and more. This gives hackers complete control over the victim’s device.
Once they have complete control over the machine, they can launch attacks against the target. They could use keyloggers, spyware, adware, Trojans, viruses, worms, bots, etc. In short, anything that would give them remote access to the infected PC. After launching whatever attack they want, the attacker sends a demand, including payment details to the victim, usually ransom money in cryptocurrency.
The average ransom demand for small businesses in 2020 was $178,000. However, this figure varies depending on when the infection occurred and when the payment is demanded. The longer the delay, the higher the amount of money requested. For example, the price tag would likely increase if you were hit with Ransomware two weeks ago but didn’t pay your ransom within 24 hours. If you waited three months before paying, the cost might double.
How do People Fall Prey to Ransomware?
There are several reasons individuals and organizations fall prey to Ransomware: lack of security awareness, poor password practices, weak passwords, phishing scams, malware infections, outdated operating systems, unpatched vulnerabilities, and other factors. Some issues are easy to fix; others require extensive training and education programs. It’s not just about knowing where to look; it’s about understanding the risks associated with each action.
Lack of Security Awareness
The most popular reason so many companies get attacked is human error, and they don’t take proper precautions to protect themselves. Employees often click through warnings without reading them carefully enough to understand what they mean. Others fail to update software regularly, which leaves them vulnerable to new threats. Even worse, some employees choose to ignore alerts altogether. All of these things put companies at risk of being hacked.
Weak Passwords
Weak passwords aren’t necessarily bad ones, per see, but they’re certainly less effective than strong passwords. Strong passwords include characters from all different categories and combinations of those categories. To help create stronger passwords, use tools such as LastPass or 1password. These applications will generate random passwords based on information stored locally on your device. This means no one else has access to your passwords except yourself. Another option is to use a password manager service instead. There are plenty available online that can be used free of charge. They’ll store your passwords securely and allow you to log into websites quickly and conveniently.
Phishing Scams
A phishing scam involves sending emails pretending to be legitimate business partners asking recipients to provide sensitive data via email attachments or links. Phishers often send out hundreds of thousands of messages every day. Their success rate can be meager because the payoff is so great. So they send all these emails out because they know it’s only a matter of time before one of their targets responds. The goal? Steal valuable financial information or login credentials for accounts held in someone else’s name.
If you receive any suspicious emails, delete them immediately. Never open attachments unless you know exactly whom they came from and what they represent. Be wary if you ever see requests for money or payment instructions. Don’t give away your private info. Instead, contact the company directly over the telephone or visit its website.
Malware Infections
The most dangerous malware infection occurs when hackers install malicious programs onto computers without permission. Malicious code may steal important files, damage system settings, corrupt databases, spy on user activity, or cause other problems. It also opens doors for cybercriminals to gain control of infected systems remotely. Hackers sometimes disguise malware infections as fake security updates or patches. It’s more likely that you’ve been hit by malware than not.
So always keep your antivirus and anti-malware solutions updated and run scans regularly. And don’t forget about backups: Backing up your computer frequently helps ensure that critical documents and photos won’t get lost due to hardware failure or accidental deletion.
Social Engineering Attacks
These attacks involve tricking people into giving up confidential information through social engineering techniques. For example, attackers may pose as friends, relatives, coworkers, or others known to victims. Once inside, they may try to obtain usernames, passwords, banking information, or other sensitive data.
Social engineers might even convince users to click on an attachment containing harmful software. Or they could pretend to have forgotten account details and ask for new ones. Victims should never disclose personal information to anyone who calls claiming to be with a bank or credit card provider. Even if the caller claims to work at the institution, they aren’t authorized to speak on behalf of the organization. Always verify this before providing any personal information. Also, avoid clicking on links sent in unsolicited emails. It would be best if you didn’t trust anything you find outside trusted sites like Google, Facebook, Twitter, etc.
Viruses & Worms
When viruses infect computers, they replicate themselves until they reach a certain size. Then they spread throughout networks using network connections. Viruses usually do nothing but slow down PCs and make things look ugly. However, some viruses can harm your PC. They may change file names, add unwanted shortcuts to desktop icons, or create duplicate copies of existing files. Some viruses are designed to destroy all data stored on hard drives. Others will encrypt files so only those with special knowledge can read them.
Still, others use stealth technology to hide within typical operating systems. These threats are called worms because they move around networks looking for vulnerable machines to attack. When they find one, they attach themselves and begin replicating. These nasty little creatures can wreak havoc on entire organizations if left unchecked.
How to Keep Yourself Safe
Ransomware has become one of the biggest threats to businesses today. The good news? There are ways to protect your business from becoming another statistic. Here are five tips to help prevent ransomware infections:
1) Keep Your Data Safely Backed Up
It sounds simple, but it isn’t. Many small to medium-sized businesses simply aren’t backing up their critical information regularly. That means they lose access to their entire company database when an attack occurs. Not only does this put them out of commission for weeks or months, it also puts sensitive customer information at risk. To avoid these problems, SMBs should back up their databases daily. This way, if something happens, they’ll have time to restore lost data without losing any customers.
2) Use Strong Passwords and 2FA
If someone manages to break into your network, chances are they already know what username/password combinations work best. So why not just change those passwords now? The answer is obvious: weak passwords leave your organization vulnerable to future breaches. Instead, choose strong passwords with unique characters. For example, don’t use “123456” as your password; instead, opt for something like “qOeErtyu!iopa1@4sdf.” You might think choosing long strings of random letters would be too difficult, but remember that hackers will often brute force their way past weaker passwords. Creating complex passwords limits the number of attempts required to crack them.
3) Install Antivirus Software on All Computers
Antivirus programs are great at detecting malware but won’t stop all types of malicious activity. Hackers constantly develop new viruses, so having multiple layers of protection is essential. If possible, install anti-malware software on every computer connected to your network. Even better, consider installing it on each device.
4) Update Malware Protection Frequently
Antivirus updates can provide additional protections against known threats. But most importantly, they ensure that your system remains protected against newly discovered vulnerabilities. Some experts recommend updating your security software once per week.
5) Be Vigilant About Email Attachments
Email phishing scams are among the fastest-growing forms of online fraud. They typically send an email containing a link that directs users to download a file attachment. Once opened, the attachment installs malware onto the user’s machine. While there are many different variations of this scam, here are three things you need to watch out for:
- Don’t open attachments unless you’re expecting them. It may seem counterintuitive, but opening suspicious emails could make matters worse by spreading malware throughout your network.
- Never click links embedded within messages. These links usually lead to websites where criminals attempt to trick victims into downloading and executing malware.
- Always verify who sent the message before clicking on anything. Most modern browsers allow you to see exactly who sent the email from its address bar. Please hover over the sender’s name until it turns blue. Then select “View Source” to view the actual source code. Make sure everything looks legitimate before proceeding.
6) Keep Your Network Up-To-Date
The same goes for keeping your network updated. Many organizations use outdated operating systems or applications. This makes them easy targets for cybercriminals looking to exploit any holes in their defenses. To avoid becoming another victim, update your devices regularly.
Why do We see New Variants of Malware Every Year?
There are three main reasons why we see so many different types of malware: 1) Malware authors keep trying to improve upon existing techniques; 2) New distribution methods make it easier than ever before to spread malware; 3) It’s highly profitable.
Malware authors try to improve their code because they realize that it will not last forever, no matter how much effort goes into writing something. Sooner or later, another author will come along and write better software. That means that even though your program might be working fine now, it won’t always stay that way. It’ll eventually get patched, updated, or replaced entirely. And when that happens, you’re left holding a piece of garbage instead of having a fully functional application.
Today, websites like MegaUpload and RapidShare offer free accounts to everyone. Anyone who signs up gets a free account and can pay around $10 per month to upgrade to premium service. Premium subscribers gain additional features like faster upload speeds and higher storage limits. While signing up for a premium subscription isn’t mandatory, users must provide personal data. With that kind of sensitive info, it makes sense that cybercriminals would start targeting these services.
The last reason is simple — there’s money in malware! Ransomware gangs make money hand over fist, banking on poor business endpoint security practices and even poorer employee training. If businesses took the time to educate their employees and deploy advanced threat protection solutions like IronScales’ anti-phishing email security software, they’d be in much better shape.
You’ve Been Hacked. Should You Pay the Ransom?

Photo by Bermix Studio on Unsplash
Never Pay Ransomware Payments! – It may seem tempting to pay up after getting hit with Ransomware but doing so only encourages more cybercriminals to continue targeting unsuspecting individuals. Instead, take steps to back up and recover your files in case of a ransomware attack.
If you don’t have backups and have to pay, consider your options first – Before paying anything, make sure you understand how much money you’ll save if you decide to pay versus recovering your data via another method. There are several factors to consider, including whether or not you want to restore your entire system or focus on restoring individual files. One thing often overlooked is backing up your data before making payment decisions. Backups should be done regularly and stored offline so that no matter what happens, you won’t lose everything or anything if you back up daily.
Please Don’t Panic! We Can Help! – No matter what kind of situation you’re facing, we’ve got you covered. Our team has been helping customers regain access to lost data for years now, and we’d love to help you too. Contact us today to learn more about our service options.
Ransomware Timeline
- Infection Process – When a user visits an infected site, malware will automatically load onto their machine without them even realizing it. Malicious code then uses keylogging and screen recording techniques to steal login credentials and personal information. Afterward, it sends copies of stolen info back to the hacker who created it, along with instructions on unlocking certain files.
- Encryption – Once the hacker receives the ransom demand, they begin encrypting the victim’s files. This process involves converting each file into a string of characters known as ciphertext. The encryption algorithm used varies depending on the specific variant of Ransomware. However, most variants utilize AES 256-bit keys.
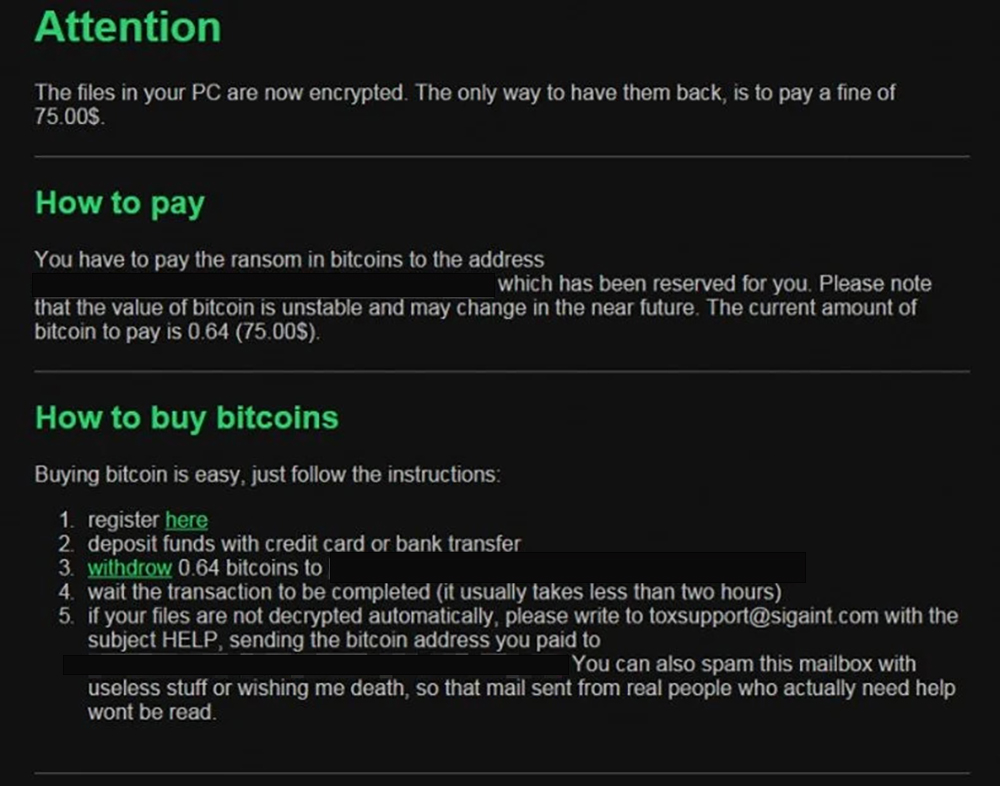
- Lock Screen Messages – In addition to locking affected files, hackers sometimes display messages on victims’ screens while they wait for payments. These messages typically include phrases like “Warning! All your files have been encrypted! If you don’t send $, all your files will remain locked forever!”
- Payment Request – Hackers usually ask for payments in Bitcoin due to its anonymous nature. They offer different amounts ranging anywhere between 0.5 BTC to 1 BTC. Some variants require multiple transactions over time to reach the final amount. For example, some variants request 10% of the total weekly sum until full payment is made.
- Unlock Instructions – Finally, once the hacker receives enough funds from their victims, he unlocks the files. He does this by decrypting the original plain text versions of the previously encrypted files.
- Recovery Process – Victims can use various methods to get their files unlocked. Users commonly try to contact the hacker directly through email or social media accounts. Alternatively, they may attempt to recover the decrypted version using software tools designed specifically for this purpose.
Final Thoughts
While there’s little doubt that ransomware attacks are increasing at alarming rates, many people still fail to take basic precautions against infection. It doesn’t hurt to keep antivirus software updated and scan suspicious emails before opening attachments. Also, never click links embedded within emails; even if you’ve gotten emails from this person before, their account may be hacked. A disaster recovery plan and backups are more important than ever imagined. Make sure you’re prepared for the worst. Lastly, if you ever need recovery assistance, make sure to call professionals instead of trying to do everything yourself.




Trackbacks/Pingbacks