
by Chad Ostreicher | | IT infrastructure, IT Network, Security, Tips
As the race to keep up with the lightning speed of technology intensifies, Zero Trust is the savvy strategy that smart companies are embracing to stay ahead of the game. Gone are the days of blindly trusting traditional security models! We must evolve and adapt to the...

by Chad Ostreicher | | Best Practices, Security, Tips
Have you ever opened your email inbox to find dozens of spam messages? If so, you’re not alone. Distributed Spam Distraction is an attack that inundates an individual or company with a deluge of messages, making it almost impossible to identify authentic...
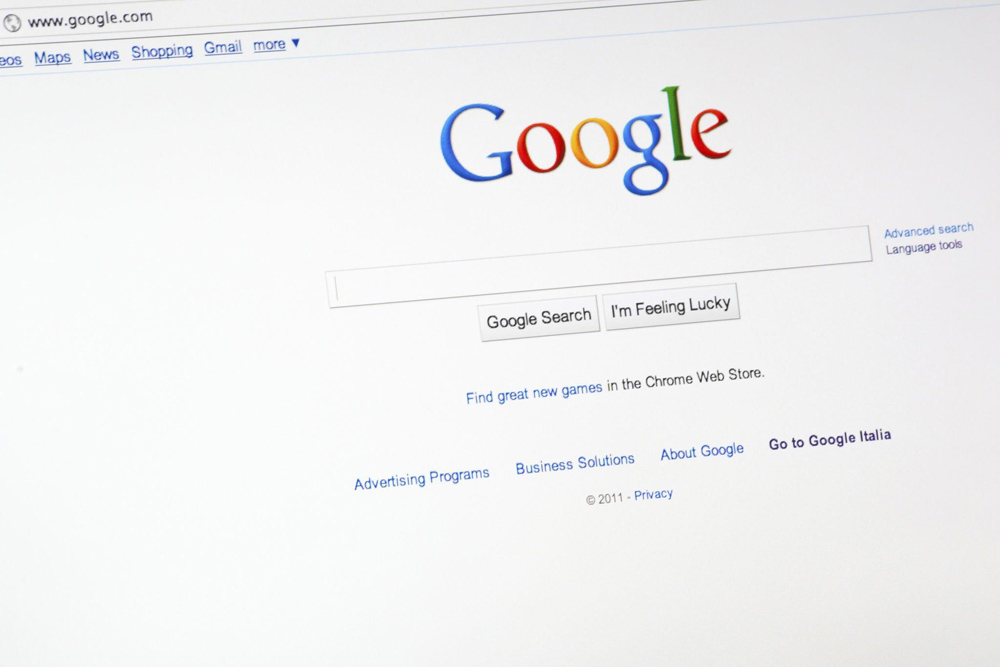
by Chad Ostreicher | | Tips
Did you know that there are hidden hacks in Google Chrome that can take your browsing experience to the next level? These hacks allow you to customize Chrome, increase productivity, and enhance security. Who doesn’t want that? One of...

by Chad Ostreicher | | IT infrastructure, IT Network, Tips
Networking is an essential part of modern life. Networking is critical to staying connected, whether streaming videos, sharing files, or connecting with friends. But what happens when your connection isn’t working? If you’ve ever experienced a dropped...

by Chad Ostreicher | | Password Management, Security, Tips
With the ever-increasing number of online services and platforms, remembering many passwords for them has become almost impossible. We’ll explore the safety of password autofill, its benefits, and its potential risks. From man-in-the-middle attacks to...

by Chad Ostreicher | | Security, Tips
We’ve all heard horror stories of online scams, but few are as insidious and dangerous as the social engineering scam. These security threats are designed to manipulate unsuspecting victims into giving away sensitive information, such as passwords and credit...







