Encryption and decryption are encryption methods that everyone should be aware of. Encryption lets us communicate with people securely, protect our data from hackers, and ensure that the information we are sending to others can’t be intercepted by anyone else. However, encryption isn’t perfect – it has its disadvantages and advantages. This post will explore encryption vs decryption, the different types of encryption algorithms, how encryption works, how you can use encryption to keep your data safe on any device or platform, and the strongest encryption algorithm in use today.
Table of Contents
What is Encryption?

Photo by Markus Spiske from Pexels
Encryption is a method of scrambling data so that it cannot be understood by anyone who might intercept the information. This encryption scrambles plaintext (unencrypted or normal text) into ciphertext, an unreadable text that can’t be read even if you have access to the encryption key and an encryption algorithm. To create this encrypted message, encryption uses encryption algorithms – complex mathematical functions used to encrypt data. If you have the encryption key, you can decrypt the ciphertext back into plaintext using encryption and decryption algorithms. These encryption algorithms generate encrypted messages, so they must be kept secret to remain secure!
What is Decryption?
Decryption is the opposite of encryption. It reverses encryption and turns ciphertext back into plaintext. This can be done using a decryption algorithm, which keeps information secure by requiring a password or PIN (also known as keys) to decrypt data. The encryption key is combined with an encryption algorithm to create encrypted messages that can only be decrypted using the encryption key and a corresponding decryption algorithm. If you don’t have the encryption keys, it’s impossible to decrypt data without them!
Encryption vs Decryption Types of Cryptography Algorithms
The age-old battle of encryption vs decryption is as old as time. There was once no such thing as encryption because everyone could easily see each other’s communications. However, as technology advanced, cryptography became more sophisticated and allowed us to send sensitive information over public networks safely. Today, encryption is widely used across many industries, including banking, healthcare, government agencies, the military, education, etc. Several forms of encryption are available: symmetric, asymmetric, hybrid, and quantum. Let’s take a look at these four main categories of encryption below.
Symmetric Cryptography
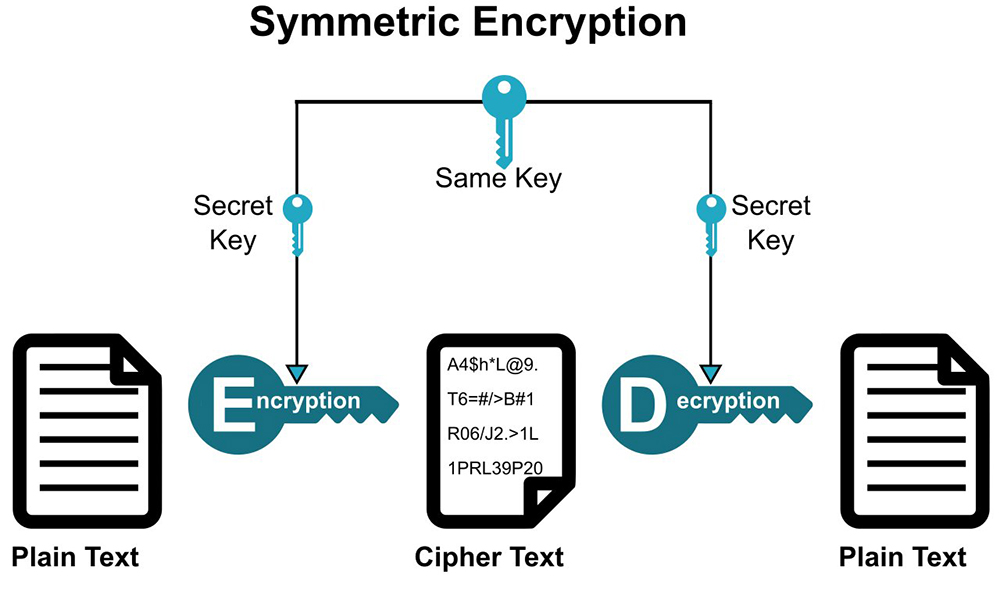
Picture courtesy of About SSL
This type of encryption method requires both parties involved in communication to share their unique encryption keys. Symmetric encryption relies on one single shared key between the sender and receiver. Once the key is exchanged, the sender sends out the plaintext along with the key. When the recipient receives the message, they then use their private key to decipher it. Since both sides know the same key, nobody but the intended recipients can decode the message.
Asymmetric Cryptography
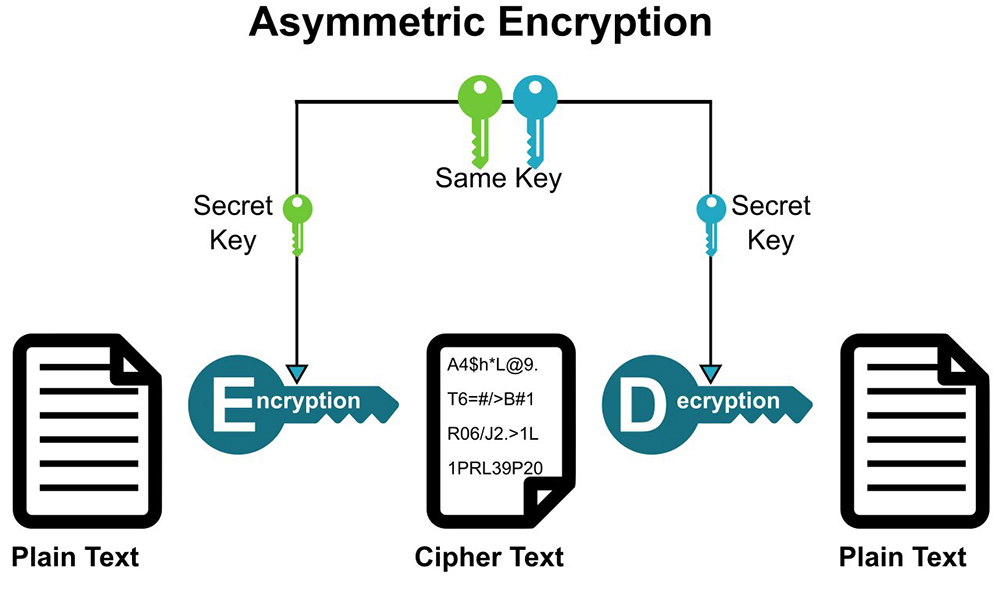
Picture courtesy of About SSL
This encryption process doesn’t require sharing a common key; instead, it creates separate keys for every user communicating. Each party holds a pair of keys – one public and one private. A public key is made publicly accessible, while a private key remains hidden. Anyone wishing to send a message to another person would first generate a new random number called a nonce. Next, the sender computes two numbers from the nonce, one being the modulus and the second being the exponent. They then multiply the modulus value by the exponent value to get the final result. Finally, the sender converts the resulting number into its decimal equivalent and writes down the digits.
After receiving the message, the recipient does the same except to replace the original nonce with the received one. If the two values match up correctly, they will produce the same results when multiplied together. However, since this method generates a new set of numbers for every message sent, it makes it very difficult for anyone else to intercept your messages.
Hybrid Encryption
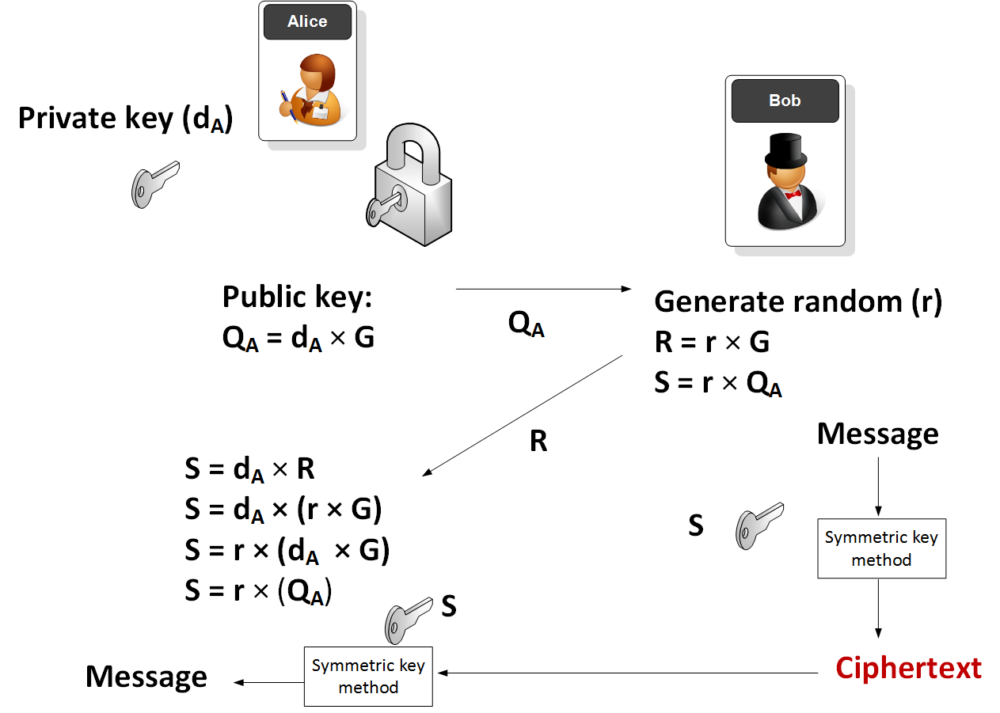
Image courtesy of Prof Bill Buchanan OBE
Hybrid encryption combines elements of both symmetric and asymmetric encryption. For example, some companies use RSA Public Key Infrastructure, where users receive certificates containing their public keys. These certificates also contain an expiration date to know how long the certificate should be valid before expiring. The company automatically keeps track of expired certificates and issues replacement ones. This way, even though only the owner has access to their private key, others still need to obtain a copy of the corresponding public key.
Quantum Cryptography
The last of the four forms of encryption technology is quantum cryptography. In recent years, researchers have been working hard to develop technologies based on quantum mechanics. Quantum computers promise to break existing cryptographic algorithms within minutes rather than hours or days. While we’re not ready to implement them commercially, scientists believe quantum computing may become a reality sooner than expected. Until then, we’ll continue using traditional methods like AES and SHA256.
How Does It Work?
Encrypting data involves taking a string of characters and converting it into something incomprehensible. To do this, you must take each character individually and convert it into a series of binary bits. You then combine all these individual bits into groups of eight bits known as bytes. To encrypt text, replace each letter with a byte consisting of 1’s and 0’s. Then, add zeros at the end until no more letters are left. If you want to decrypt the encrypted file back to readable text, reverse what was done during encryption.
Let’s look at an easy-to-understand simple encryption example:
Let’s say I want to write down my name. I start off writing “John Smith” and convert it into ciphertext. Before sending this out, I decided to include a secret code at the beginning of the ciphertext. So now, my ciphertext reads “JHN S M T.” Once I receive this, I know that John Smith must be hiding behind the code. But how did he hide his identity without me knowing about it? He added a few more letters to the front of the ciphertext. The first letter, J became H, and the second, N became P, etc… By adding enough additional letters, he could disguise himself completely.
Encryption-Decryption Process
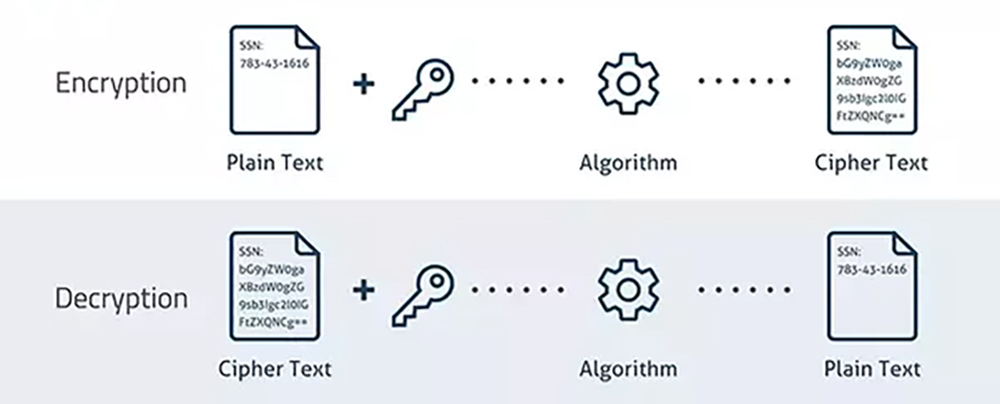
The main difference between encryption and decryption is that encryption requires a shared secret key, whereas decryption uses a single secret key. When someone sends you a piece of information, you can either read it directly or pass it through an algorithm that changes it slightly. Both processes involve changing the content, but only one needs a shared secret key. Let’s look at some others below:
- Encryption turns plaintext into ciphertext (unreadable data) or vice versa
- Decryption is the opposite of that – it can turn ciphertext back into plaintext to be reread. It requires an encryption key and a decryption algorithm.
- Encryption algorithms are what create encrypted messages and encryption keys. They must be kept secret to remain secure!
- Decryption is the opposite or reverse of encryption. It reverses encryption by turning ciphertext back into a plaintext message – this can only be done using a decryption algorithm and an encryption key.
Encryption has its advantages as well as its disadvantages. The advantages of encryption technology are that it can be used for digital security, including secure communication and keeping data safe from prying eyes when transmitting information over the internet or even locally on your device. However, encryption isn’t perfect – if you lose your encryption key or forget the password required to decrypt an encrypted message (the decryption key), you won’t be able to read the information contained within. This encryption key is also used in combination with an encryption algorithm. If someone obtains access to this encryption key, they could decrypt all your encrypted messages and even use it for their purposes!
This disadvantage can be advantageous, as criminals would need both your encryption key and password to decrypt your data if you lose it or forget the encryption keys. To use this against you, criminals need physical access to both pieces of information to decrypt any encrypted messages created using these encryption methods – increasing encryption security!
One of the main benefits of Encryption technology is that it’s used by businesses and individuals to keep their data secure. As encryption is key-based, only those with the encryption keys can access and read an encrypted message, protecting it from hackers looking to steal information!
Decryption also has its advantages and disadvantages as well – on the one hand, you don’t need a decryption key or password if you lose your device (as long as encryption is used properly). However, if you lose your decryption key or forget the password required to decrypt an encrypted message – you can’t read any of its contents! This means that encryption isn’t perfect and presents a risk when transmitting information over the internet.
How Does Cryptography Work?
Cryptographic systems consist of three main components:
1. Algorithms – These are mathematical functions designed to encrypt/decrypt text. Many different types of algorithms are available, such as symmetric ciphers, asymmetric ciphers, and hashing algorithms.
2. Keys – A cryptographic system needs two things to function; firstly, there needs to be some way to generate random numbers to know how to perform operations like addition and multiplication without relying on chance alone.
3. Modes of Operation – Cryptography modes allow us to combine multiple algorithms to create more complex codes. For example, AES uses CTR and CBC modes to provide confidentiality, integrity, and authentication.
The most important part of the cryptographic system is the algorithm. Cryptographic algorithms are mathematical operations performed over data. Many algorithms are available, including symmetric cryptography, asymmetric cryptography, block cipher modes, stream cipher, hashing, MAC, etc.
Symmetrical cryptosystems operate under the assumption that all participants share identical secret keys. Symmetrical cryptosystems include DES, 3DES, Blowfish, RC5, IDEA, RSA, ElGamal, DSA, DH, ECC, SHA-256, MD5, HMAC, KDF, PBKDF2, etc.
Cryptography Stack Exchange

Photo by Yelena Odintsova from Pexels
What’s a crypto stack exchange? It’s a question we often hear when people first start learning about security. “I want to learn about crypto! Where do I go? What resources exist? How do I find out about new developments?”
A Crypto Stack Exchange is exactly what its name implies — a place, most likely an online community, where all things crypto meet up.
What is the Strongest Encryption Algorithm?
The strongest encryption algorithm is currently considered to be quantum-resistant. Even though quantum computers are still years away, it would take millions upon millions of dollars in computing power to crack these types of ciphers.
There are various ways to measure the strength of an encryption algorithm. One way is to compare its security against brute force attacks. A brute-force attack involves trying all possible combinations until the correct combination is found. Another method compares the time taken to break down the ciphertext into plain text.
Which type of cryptosystem is better suited for securing sensitive data?
Symmetric crypto algorithms require secret keys to operate correctly. Symmetric crypto algorithms provide confidentiality because they prevent eavesdroppers from reading the contents of transmitted messages. However, symmetric crypto algorithms do not protect against man-in-the-middle attacks. In this attack, someone intercepts communications between you and your intended recipient. This attacker impersonates the sender, so he appears legitimate while capturing everything communicated.
To avoid this kind of attack, asymmetric crypto algorithms are preferred. Asymmetric crypto algorithms use different keys for sending and receiving messages. These keys must be kept secure since any future communications would become vulnerable if compromised.
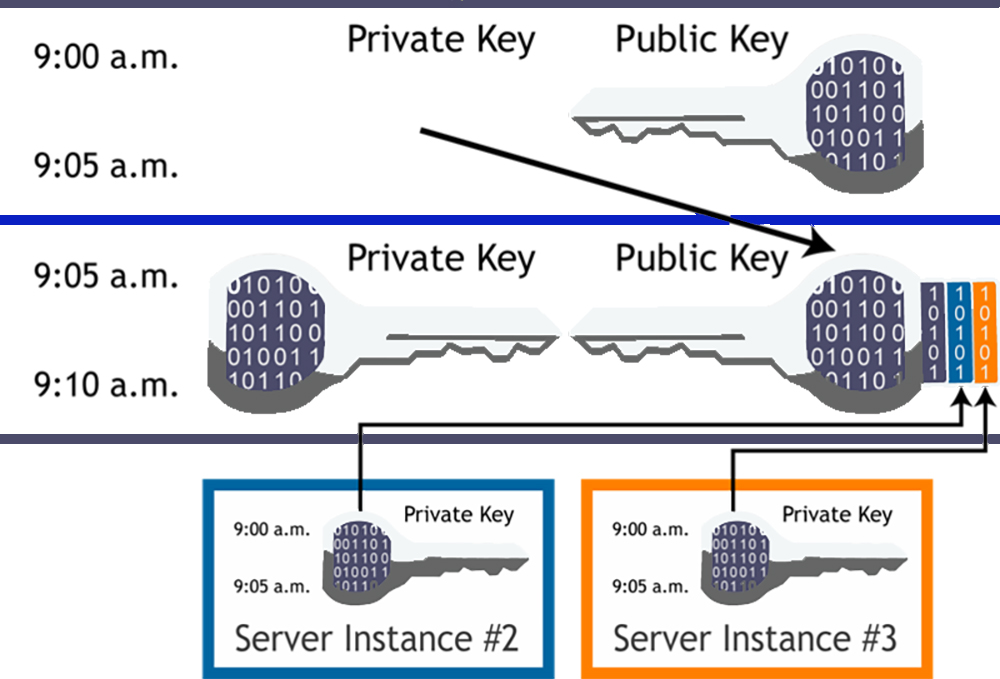
Encrypting Data with Public Key Cryptography
Public key cryptography uses two different types of keys; public and private. A public key is made available to everyone, while a private key remains confidential. With public-key crypto, users create a pair of keys known as a public/private key pair. One user generates a public key and keeps it in a safe place, such as a bank vault.
Anyone wishing to communicate securely with him must generate matching private and public keys. These keys are exchanged using digital signatures and verified through a mathematical algorithm. Only someone holding both the corresponding private and public keys can successfully verify the signature. In addition, the sender cannot use the private key to sign messages since doing so would compromise security. Instead, only the receiver holds the private key, which allows him to unlock the message once received.
Encrypted data sent between parties using public-key cryptosystems is typically signed by the sender using their private key. On receipt, the recipient verifies the signature’s authenticity using the sender’s public key. As a result, neither party ever sees the other’s private keys.
This means that even if an attacker could steal your private key, they wouldn’t be able to decrypt any encrypted communications you may have had with others.
Decrypting Encrypted Data with Private Key Cryptography

Photo by Karolina Grabowska from Pexels
Private key encryption works exactly the opposite way of public key encryption. Rather than generating a public/private key pair, the sender creates a private key and sends it along with the encrypted message to the intended recipient. The recipient has access to the private key and can decrypt the message. However, the sender never reveals his private key to anyone except the intended recipient.
This encryption method also gives us a significant advantage over public-key systems – integrity. Since the sender always knows who owns the private key used to decrypt the message, he can check whether the message was altered during transit. The sender will not accept the message if there is evidence of tampering or corruption.
The above example shows why we need to keep our private keys secure. Even though encrypting data with a public key system offers some advantages over traditional methods, it comes with risks. For instance, if you lose your private key, your previously encrypted information becomes inaccessible.
In contrast, when using private key encryption, you don’t have to worry about losing your private key because no one else but yourself should possess it. You send your private key along with the encrypted message, and the recipient can easily retrieve it wherever they store their private key.
What Types of Encryption Algorithms should you use?
It depends on what you want to achieve. The best thing to do is ask yourself why you want to implement encryption. Is it to ensure that only people who know the passphrase can access the information stored in the database? Or maybe you want to ensure that only authorized users can view certain parts of the website? Whatever your reasons, there’s probably something out there that will suit your needs, so speak to your IT professional to see what level of security they recommend.
If you have any questions about our encryption process or the types of cryptography algorithms we use, send us a message. We are always happy to answer your questions and provide more information on how our technology can help safeguard your data against cyberattacks.




Trackbacks/Pingbacks