Cybersecurity is a determining factor for today’s companies and organizations. There are latent threats to the development of any corporate activity; however, these latent threats can be defused if the appropriate mechanisms and protocols are applied.
Table of Contents
NIST Cybersecurity Framework Introduction

There isn’t a hacker brave enough to attempt to hack your network with a cybersecurity team like this. These US Department of Commerce cybersecurity experts are some of the best in the business.
NIST is the National Institute of Standards and Technology, part of the United States Department of Commerce. The NIST cybersecurity framework is a set of guidelines and rules that private sector businesses must follow to stay safe from cyber attacks. This is not limited to just private sector businesses and can be practical for supporting all businesses, regardless of their size and areas of expertise. If you want to understand your current cybersecurity solution’s levels of protection and the associated risks, you’ll need to speak to a professional. Managed IT services companies can protect your network and data and help you keep hackers at bay.
The great differential value of NIST’s Cybersecurity Framework is that it is not based on academic theoretical discourse. Still, it helps by bringing you down to the entire field of play with information, examples, and eminently practical references. The application of this framework is, therefore, much more accessible and beneficial. This set of proposed practices makes it easier to determine priorities and in which areas of cybersecurity it is essential to apply the time and money available at any given time.
NIST Cybersecurity Implementation Levels
Determining your business’s risk management level and the NIST cybersecurity framework go hand in hand when doing the most to keep your business’s data safe.
These NIST cybersecurity tiers provide context on how an organization views its cybersecurity risk and the processes implemented to manage it. The tiers describe the degree to which an enterprise’s cybersecurity risk management practices exhibit the characteristics defined in the framework. Furthermore, implementation levels characterize a company’s practices, from partial to adaptive. These levels reflect a progression from informal and reactive responses to agile and risk-informed approaches. When selecting a tier, the company should consider its threat environment, legal and regulatory requirements, business/mission objectives, and organizational constraints.
Five Areas of NIST Cybersecurity Framework Activity
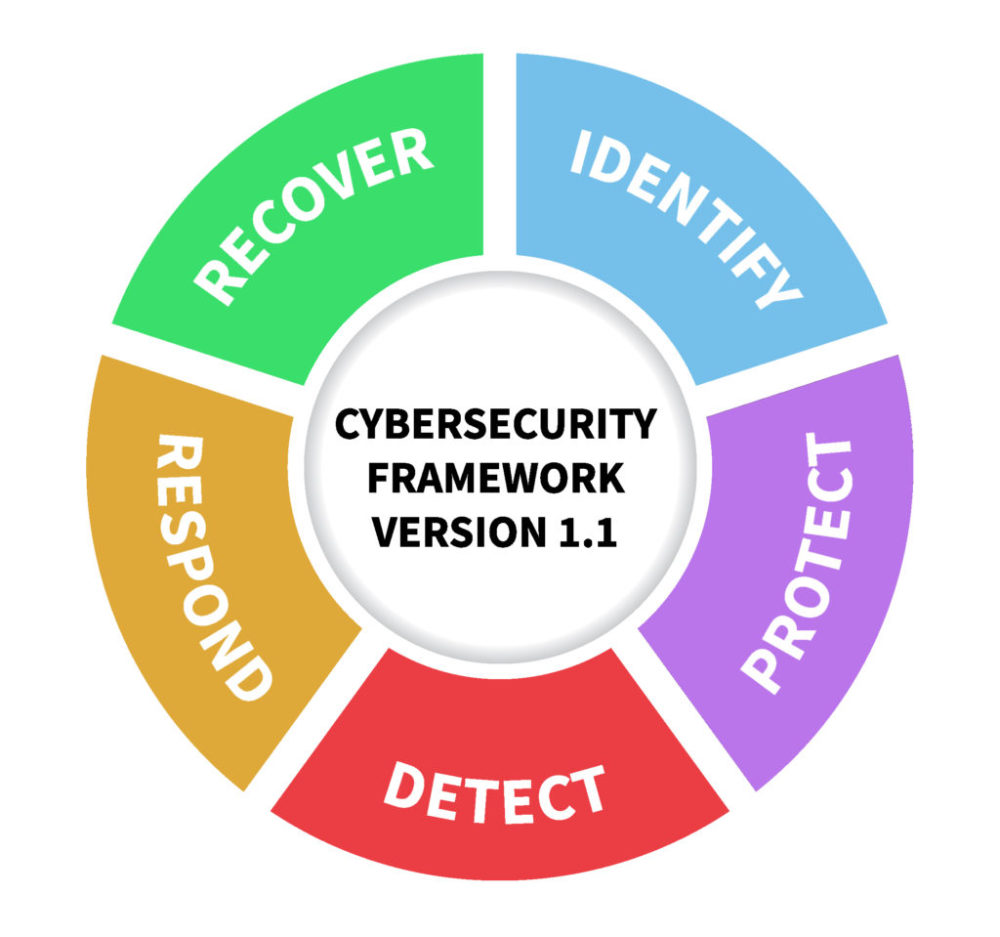
The NIST cybersecurity framework is broken into five areas, as seen below. Each area works cohesively with the other to enhance your business’s cybersecurity.
The action protocol proposed in this framework is divided into five consecutive and permanent stages. If you are clear about them and know what to do in each of them, the protection of your business will grow exponentially.
-
Identification
First, you must know the reality, establish the potential risks and take an inventory of the hardware, software, data, and electronic devices you use. Based on this information, you have to design, implement and share with your employees a concrete cybersecurity policy that includes the following:
- Roles and responsibilities.
- Action protocol, detailed by steps, to be followed in case of cyber-attack.
-
Protection
This phase includes the implementation of measures to control access to networks and devices, the use of protection programs, the encryption of data stored and in transit, regular backups, the continuous updating of programs, the definition of secure protocols for deleting files and equipment, as well as the training of all persons involved in the activity.
-
Detection
You have to be alert. The whole company, the people who form it, must be vigilant. This entails monitoring computers to determine if unauthorized persons are accessing them and the devices you use, the data, or the software used. Likewise, and with the same objective, you should check your networks and investigate any unusual or suspicious activity. This measure of action must also be applied to the efforts of your personnel. In the event of an alert, you must be aware of it as soon as possible.
-
Response
When so much is at stake, improvising is not an option. Therefore, it is essential to implement a previously defined action plan to stop the security attack and mitigate its possible negative consequences as soon as possible. In this phase, you should consider several different actions:
- Inform customers and all those who may be affected by it.
- To ensure the maintenance of the business or professional activity.
- Notify those responsible and the authorities.
- Investigate and combat the threat.
- Carry out an update of the cybersecurity policy and plan to incorporate all new developments and lessons learned.
- Be prepared for any new incident or unexpected factor.
-
Recovery
After stopping and deactivating the threat, the problem is resolved by repairing and restoring all affected elements. In this sense, it is also important to inform customers and employees of the progress, improvements, and new actions developed.
NIST Cybersecurity Frame Core
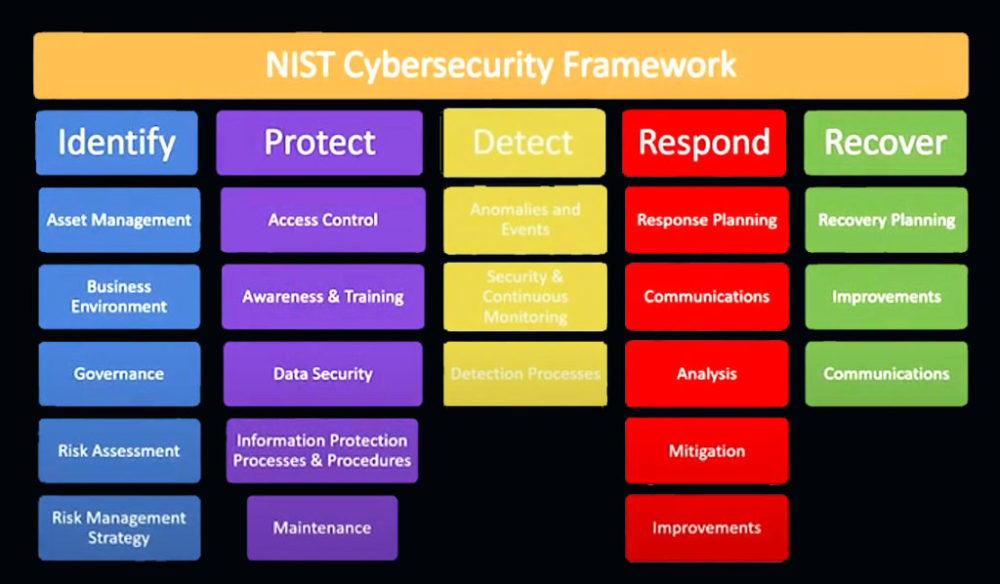
The NIST cybersecurity frame core is broken up into categories and functions. There are five categories, followed below by their functions.
The core provides five continuous functions, as seen above. It also offers activities to achieve specific cybersecurity outcomes and references examples of guidance for achieving those outcomes. The core is not a checklist of actions to be taken. It presents the key cybersecurity outcomes identified by the industry as helpful in managing cyber risk. It comprises four elements: functions, categories, subcategories, and informative references.
Would you like to learn more about the NIST Cybersecurity Framework? Would you like the support of a specialized company to implement it in your business? At Infinity Solutions, we can help you set up for cybersecurity success. We are a technology company specializing in all kinds of activities and tasks related to cybersecurity for companies and professionals.
Our cybersecurity services also focus on five areas that coincide with the stages of the NIST Cybersecurity Framework already mentioned: identify, protect, detect, respond, and recover. We provide you with a comprehensive vision, cybersecurity monitoring, and permanent support. Contact us now and prepare for future cybersecurity problems before they happen.


Recent Comments