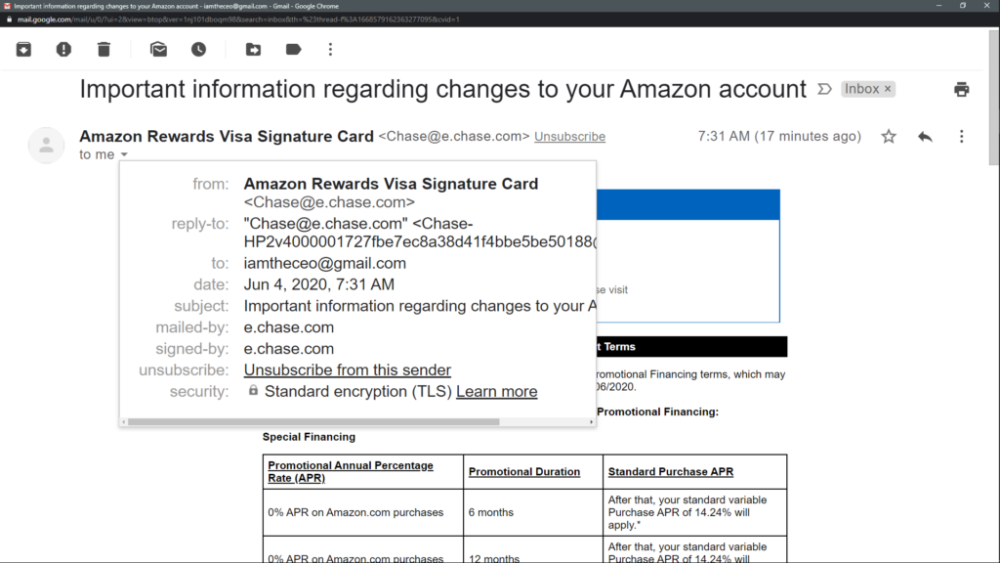
If you’ve been following the news lately, you’ve probably noticed a growing trend in recent malware attacks like the Colonial Pipeline, Kaseya, Synnex, Fujifilm, and the Salvation Army have all made headlines in the past month or so. Ransomware, which has been around for over a decade and is a type of malware, is becoming increasingly popular as a cybercrime tool. It has been known for many years to be used by cybercriminals to extort money from victims. Still, in recent malware attacks, cybercriminals have noticed and adapted to the demand by creating new, more intricate, and complex ransomware.
Table of Contents
What is Ransomware, and How Does it Work?
Image courtesy of Cloudwards
Ransomware is malicious software that blocks access to your files or encrypts them until you pay. The most common ransomware today appears on computers through spam email messages. But it doesn’t take much effort to download ransomware onto your computer manually. Often, all it takes is opening an attachment from an unknown sender who claims they found something suspicious on your PC.
Once installed, ransomware can lock your screen and display a ransom note pop-up demanding payment before allowing you back into your system. In some cases, ransom demands may include threats against family members or other personal information like leaking compromising photos and videos of the victim. Hackers will delete everything on your hard drive if you don’t comply with their demands within a certain amount of time.
Ransomware works because hackers have figured out how to exploit vulnerabilities within Windows and Apple operating systems. They exploit bugs already in older versions of Microsoft Windows or install backdoors onto vulnerable servers.
When a victim opens their email account or clicks on a link sent via text message, they unknowingly download a piece of code that allows the attacker to remotely control the victim’s computer. This means that the hacker has full control over everything that happens on the victim’s PC. From here, the hacker can install additional malware onto the compromised server, steal sensitive data, or even delete important documents.
Once installed, the malware will begin searching for certain keywords and phrases that may help identify the owner of the affected computer. If it finds anything suspicious, it will attempt to contact an online payment service provider to request a ransom demand. The hacker usually asks for a ransom before unlocking the encrypted files with a decryption key. While some ransoms start at only $50-60, others go much higher.
Some hackers will offer to decrypt the files if they pay them directly using cryptocurrency, a credit card number, or a PayPal account. Others will hold all the files hostage until the victim agrees to pay whatever ransom was requested.
Some Notable Ransomware Cyber Attacks
Image courtesy of Bleeping Computer
The biggest ransomware attack before 2021 was the WannaCry Ransomware incident which targeted over 230,000 organizations across 150 countries in May 2017. But in 2021, we have eclipsed the record previously held by WannaCry with the three largest ransomware attacks.
The largest ransomware attack in history was perpetrated by the ransomware gang known as REvil on July 2, 2021. REvil is a Russian-linked hacker organization that breached Kaseya’s VSA software and brought around 1500 MSPs and businesses worldwide to their knees. We are sure the number is much greater since the MSPs affected managed clients, but Kaseya reports around 1500 affected businesses.
REvil demanded a ransom of 70 million dollars in cryptocurrency, and once received, they would post a universal tool that would decrypt affected servers and systems. This left Kaseya scrambling, and we are confident that a ransom was paid; how much is unknown because, by July 21, they had the decryption tool.
The second-largest ransomware attack to date is the assault on Taiwan-based PC producer Acer that brought about the highest payment request ever: $50 million. On March 18, a post on REvil’s site contained an extensive rundown of monetary records. It connected to REvil’s ransomware demand of $50 million in Monero, XMR, which was to be paid by the ransomware victim, Acer. REvil posted some screenshots of banking documents stolen from Acer, but Acer never admitted to being breached, and it’s hazy if the PC producer paid the ransomware payment.
The third-largest ransomware attack was against one of the largest insurance companies in the U.S. on March 21, causing an organizational disturbance at CNA Financial. Unlike the two above, this attack was not performed by REvil. Still, another Russian hacker group called Evil Corp. Either way, CNA Financials’ data was encrypted, and they ended up paying $40 million to the ransomware gang to decrypt their files.
Different Types of Ransomware
Image courtesy of Geek’s Advice
There are three main types of ransomware; Cryptowall, Locky, and Cerber. Each has its unique features and capabilities. Let us look at each of them to know what to expect when dealing with these malicious programs.
CryptoWall – CryptoWall is considered to be the first form of modern-day ransomware. The name comes from this strain encrypts all user files using AES encryption technology. In addition to file encryption, CryptoWall also includes other tactics, such as locking down infected computers or demanding payments through Bitcoin wallets. These demands can range anywhere between $500-$1000 depending on the severity of the infection and the amount of damage done.
Locky – Locky is similar to CryptoWall in terms of functionality; however, there are several differences in this type of ransomware. Instead of encrypting your files, Locky will lock users out of their computers until they pay off a ransom demand.
Once again, the price varies based on the level of damage caused by the virus. Another difference is that Locky does not include decryption software like CryptoWall. Instead, it simply locks people out of their machines unless they pay up.
Cerber – Like Locky, Cerber is also a variant of ransomware. However, while Locky and Cerber use the same basic functions, Cerber differs slightly in using different methods to get into the system.
Unlike Locky, Cerber doesn’t require any keylogger or trojan horse to access the machine. Instead, Cerber relies solely on brute force password cracking techniques to allow the ransomware attackers to enter the system. As soon as it gets inside, it spreads throughout the network and infects every device. After that point, it starts looking for specific information, including passwords, financial details, social security numbers, etc., and then proceeds to encrypt those items.
How To Protect Yourself From Ransomware Attacks

Image courtesy of Varonis
The first step towards protecting yourself from ransomware is education. Educating your employees on proper internet usage is more crucial than ever. Educating your staff will help prevent them from opening emails they don’t recognize. If you suspect your employee opened such an email, please get in touch with us immediately.
You should always make sure to keep anti-virus programs updated so you can detect and remove any potential threat quickly. Also, avoid clicking links sent via social media like Facebook or Twitter unless you trust the source. Finally, when downloading anything off the internet, use reputable sources such as Google Chrome instead of third-party apps. These sites offer better security features than others.
It seems like every day, we hear about another major hack attack. Hackers seem to be getting smarter and finding easier ways to get inside people’s systems. While there isn’t a foolproof method to prevent being hacked, there are things you can do to minimize the risk. For example, never give out sensitive information over unsecured networks. Always log out after browsing certain web pages. And finally, install antivirus software and update it regularly.
How Do I Know if My Computer Has Been Infected With Ransomware?
There are several ways to tell if your computer has been infected with ransomware. First, when you open your browser, there should be no advertisements asking you to upgrade your operating system. Also, you shouldn’t see any pop-ups telling you about updates available. Lastly, you should never receive unsolicited phone calls claiming to be from Microsoft or another company.
These scams usually come after someone opens an email containing malicious files. The first step towards recovery is knowing whether or not your system has been attacked. The second step is contacting your security experts and having them remove whatever threat may still exist on your PC.
Ransomware Removal Steps:
Step 1 – Remove Malicious Software From Your System
The most important thing to remember here is that we cannot guarantee 100% malware removal once it has entered your system. We recommend running an anti-malware tool before attempting to restore your data. We use SentinelOne, and so do our clients. SentinelOne is extremely proactive at preventing malware from ever entering your network, let alone infecting your computers. But if you aren’t using SentinelOne, you’ll want to back up your documents and photos before removing anything else. Once these steps have been completed, proceed to Step 2 below.
Step 2 – Restore Data Files & Applications
The next step would be restoring your data files and applications from a backup. This process could take some time, depending on how much of your data was affected.
Step 3 – Clean Up Remaining Viruses/Malware
This final step involves cleaning up remaining viruses and other malware. Again, this depends on what exactly happened during the infection. Some infections might leave behind only traces of themselves, whereas others might cause significant problems. Please note that you’ll want to speak with your cybersecurity expert before restoring your data.
Ransomware vs. Malware

Image courtesy of Comodo Enterprise
The difference between ransomware and malware is pretty simple. A virus infects files on your hard drive, whereas ransomware encrypts them. Once encrypted, they cannot be opened until a ransom amount is paid. Does this mean viruses are less dangerous? Not at all! Viruses cause damage just as much as ransomware does.
They may even spread faster since they aim to replicate themselves across your machine. Which one is easier to recover from? That depends entirely on how fast you catch it. If you don’t pay up within 24 hours or the time specified, then the chances are good that you won’t ever see your data again. But if you take action right away, you could save yourself some serious trouble.
Why Do People Pay to Get Their Data Back After an Attack?

Photo by David McBee from Pexels
When an attacker gains access to your personal information, he will often try to blackmail you into paying him money to regain control of your device. This is called “ransomware extortion” because hackers threaten to delete everything on your system unless you agree to pay them.
There are two main reasons why people choose to pay: 1.) Because they want to stop the hacker from deleting their data; 2.) Because they believe they can afford it. Either reason is valid. However, most people who fall victim to these scams would not consider themselves wealthy enough to pay someone thousands or tens of thousands of dollars to retrieve their data. So what makes them think they can afford it anyway? Well, here are three common misconceptions that make people feel justified in paying up:
1) You Have Nothing Of Value On Your Device – Most people assume they need to pay up to restore their lost data. However, this is simply false. Even though your data might be important to you, there’s no guarantee that anyone else cares about it. Hackers do not care whether or not you lose any particular piece of data. All they want is your money. Therefore, you should focus instead on protecting your valuable assets like financial accounts, social security numbers, passwords, credit card details, etc., rather than worrying about losing specific pieces of data.
2) You Can Afford It – Another misconception is that you must pay up because you can’t afford to replace your stolen data. While it’s true that you shouldn’t spend every penny you earn, you also shouldn’t let fear dictate your spending habits. The truth is that you can always find ways to cut back on expenses without sacrificing quality. For example, you can use online services such as Google Drive or Dropbox to store large amounts of sensitive documents. Or maybe you can switch to using free software programs instead of expensive ones. Either way, you’re at risk if you aren’t backing up your data regularly.
3) Someone Else Will Take Care Of It – Another major misconception is that others will come along and rescue you once you pay up. Unfortunately, this isn’t necessarily the case. Sometimes other parties get involved and end up making things worse. If you don’t take action immediately, you could potentially wait weeks or months before getting your files back. You may miss critical business deadlines, school assignments, tax returns, etc. If you fail to act quickly, you risk being charged with fraud or identity theft.
Can You Recover From a Ransomware Attack?

Photo by Andrea Piacquadio from Pexels
That all depends on whether or not you have backups in place and how quickly you act. When an attacker gains access to your system, he usually wants to encrypt everything so that nobody can recover anything. Once encrypted, however, most ransomware applications allow users to decrypt their files for free.
1) Get in touch with your IT professional IMMEDIATELY! They should be able to help you figure out how to unlock your files.
2) Use a third-party recovery program. Some companies offer these kinds of products for sale. Others sell them for free. We recommend using one of the latter options.
3) Contact law enforcement officials. Contact local authorities immediately if you suspect someone broke into your device and stole important financial records.
What is the Best Way to Recover My Files?

Photo by panumas nikhomkhai from Pexels
There’s no doubt about it: Nothing beats having backups available when recovering files. But not everyone has time to create regular backup schedules. That’s why you can have your IT team automate your backups. You might also want to consider cloud storage solutions. Cloud services provide online file-sharing capabilities that work across multiple platforms. And they’re easy to use because there’s little setup required. Whichever method you choose, you will be in a much better position than if you did nothing.
Why is Employee Security Education so Important?
Image by John Klossner
Phishing emails are often sent to unsuspecting individuals who may think they’re receiving something legitimate. They could even appear to be coming directly from their bank or financial institution. But if you receive a suspicious message claiming to be from a company you know, don’t click on any email attachments or links provided within the message. Clicking on a malicious attachment could lead to your entire network being compromised.
Instead, visit the website where you originally received the message to verify its legitimacy. You can also report phishing messages to us using our online form. We also use an email security software called Ironscales that monitors and filters suspicious messages.
How do I Protect Myself From Email Scams?
When dealing with unsolicited emails, it would be best to keep several things in mind. First, make sure you only open attachments from people you trust. Second, avoid clicking links inside those emails. Third, check out the sender’s address; this helps identify whether the person sending the email is trustworthy. Finally, consider contacting your local law enforcement agency if you believe someone might be attempting to scam you.
What Happens After I Get Scammed?
Once you fall victim to a scammer, there isn’t much you can do except try to recover what you lost. If you lose personal information like credit card numbers, Social Security numbers, account passwords, etc., you need to contact the appropriate authorities immediately to avoid misusing these details. In addition, you’ll want to file a complaint with the Federal Trade Commission and the state attorney general’s office. The FTC will investigate identity theft claims, while the state AG’s office will handle fraud-related complaints.
Wrapping Up
Ransomware is a severe threat because it takes control of your computer without permission. However, there are ways to prevent such an occurrence. First, always update your software regularly. Second, never click on suspicious links found in email messages. Third, use strong passwords when logging onto any website. Finally, back up your data regularly. In addition, don’t hesitate to reach out to your IT professionals to get assistance. After all, they know the steps to secure your network from recent malware attacks.